According to International Data Corporation, 90% of new enterprise applications will be cloud-native driven by agile methodologies and architectures driven by APIs. The technological and cultural changes driven by these architectures help organizations embrace change and become more nimble and speed-up their go-to-market. However, all of this does not come without its fair share of challenges.
Gartner has predicted that by 2025, 98% of failures in cloud security will be caused by the end-user organization. This is a clear indicator that security of applications is growing to be a bigger concern for organizations than the underlying cloud infrastructure.
It has been reported that 84% of safety incidents occur on the application layer. By following application safety measures, the weaknesses and vulnerabilities of a software program application are diagnosed and dealt with early on in the development cycle and do not evolve into serious security breaches.
Application Security Threats: The Top 10 OWASP (Open Web Application Security Project)
There are numerous security threats that affect software applications. However, the Open Web Application Security Project’s (OWASP) Top 10 list compiles the most common and severe application threats that affect application development.
1. Injection – Code injection includes requests, queries, or commands sent to software applications that contain malicious or untrusted data. SQL injection is the most common, but it can also affect NoSQL, operating systems, and LDAP servers.
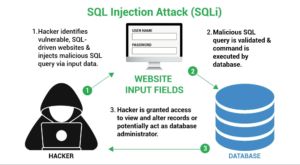
2. Broken Authentication – Many applications have inadequate or flawed authentication and authorization features. This allows attackers to steal users’ credentials or easily gain access without proper credentials.
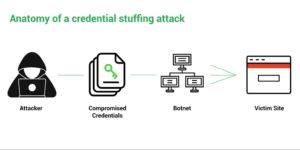
3. Sensitive Data Exposure – Applications and APIs may publicly disclose sensitive data belonging to an organization or its customers, including financial or payment data and personal identifiable information (PII).
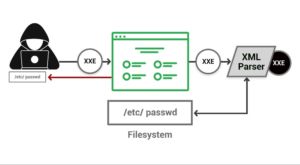
4. XML External Entities (XXE) – A vulnerability in an outdated XML parser could allow an attacker to maliciously use external object references in XML documents. It can be used to access internal files, scan ports, and run code remotely.
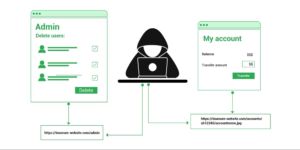
5. Broken Access Control – Authenticated but not authorized users are not implemented correctly. Attackers can use it to access unauthorized features or data, access another user’s account, view sensitive files, or change another user’s permissions.
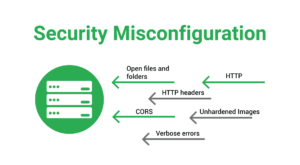
6. Security Misconfiguration – Even if the application has security features, it may not be configured correctly. This usually happens because no one has changed the default configuration of the application. This includes not applying patches to operating systems and frameworks.
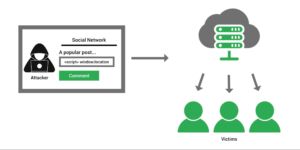
7. Cross-Site Scripting (XSS) – An attacker could run malicious scripts in the user’s browser. It can be used to steal sessions, redirect users to malicious sites or perform website damage.
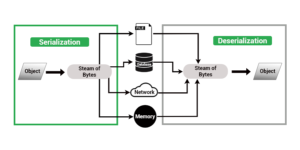
8. Insecure Deserialization – If there is an error in how to get the code from the file and convert it to an object. This can lead to malicious code execution, privilege escalation, and replay of actions by authorized users.
9. Components with Known Vulnerabilities – Several vulnerability databases report known vulnerabilities in software components. The software that uses the vulnerable component (even a dependency of one of the components) is attacked.

10. Insufficient Logging & Monitoring – Many applications may not have the means to identify or log hacking attempts. This could mean that the violation goes undetected and the attacker can move sideways and compromise additional systems.

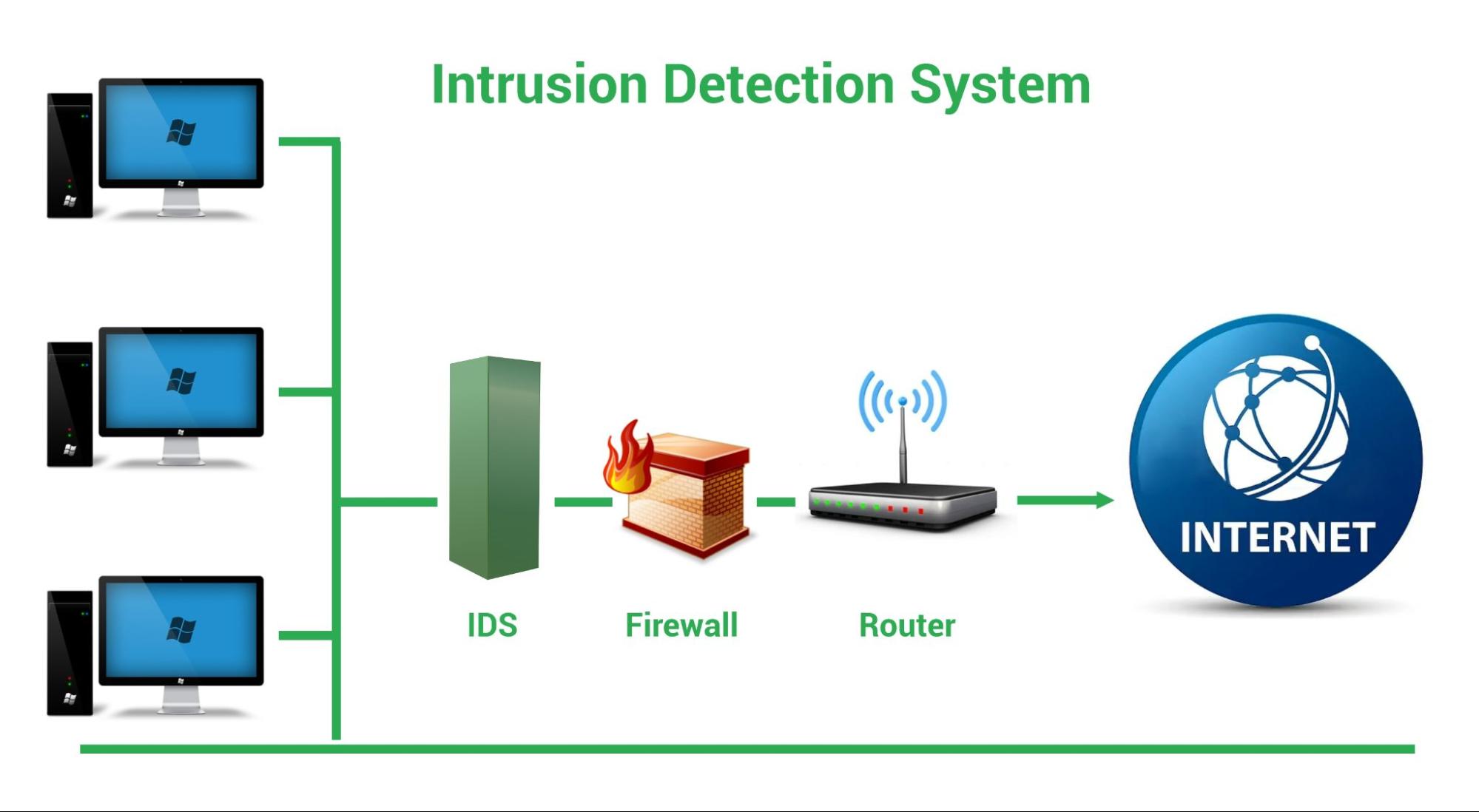
Intrusion Detection System (IDS)
A monitoring system that identifies suspicious activity and generates alerts is known as an Intrusion Detection System (IDS). A Security Operations Center (SOC) analyst or incident responder can analyze the issues and take the required steps to mitigate the threat supported by these notifications.
Classification of Intrusion Detection Systems
Intrusion detection systems are developed and designed to be deployed in different environments. An IDS, like many other cybersecurity solutions, can be network-based or host-based.
Host-Based IDS (HIDS): A host-based IDS is installed on a specific endpoint to defend it from both internal and external threats. An IDS with this capability might be able to monitor network traffic to and from the machine, see active processes, and examine the system’s logs. The visibility of a host-based IDS is limited to its host machine, limiting the context available for decision-making, but it has extensive access into the host computer’s internals.
Network-Based IDS (NIDS): An IDS system that monitors an entire protected network is known as a network-based IDS. It has complete insight over all network traffic and makes decisions based on packet metadata and content. Although this broader perspective provides greater information and the potential to detect widespread threats, these systems lack visibility into the internals of the endpoints they defend.
Because of the various levels of visibility, adopting a HIDS or NIDS in isolation only provides a partial level of protection for an organization’s system. More complete security can be provided via a unified threat management solution, which integrates several technologies into a single system.
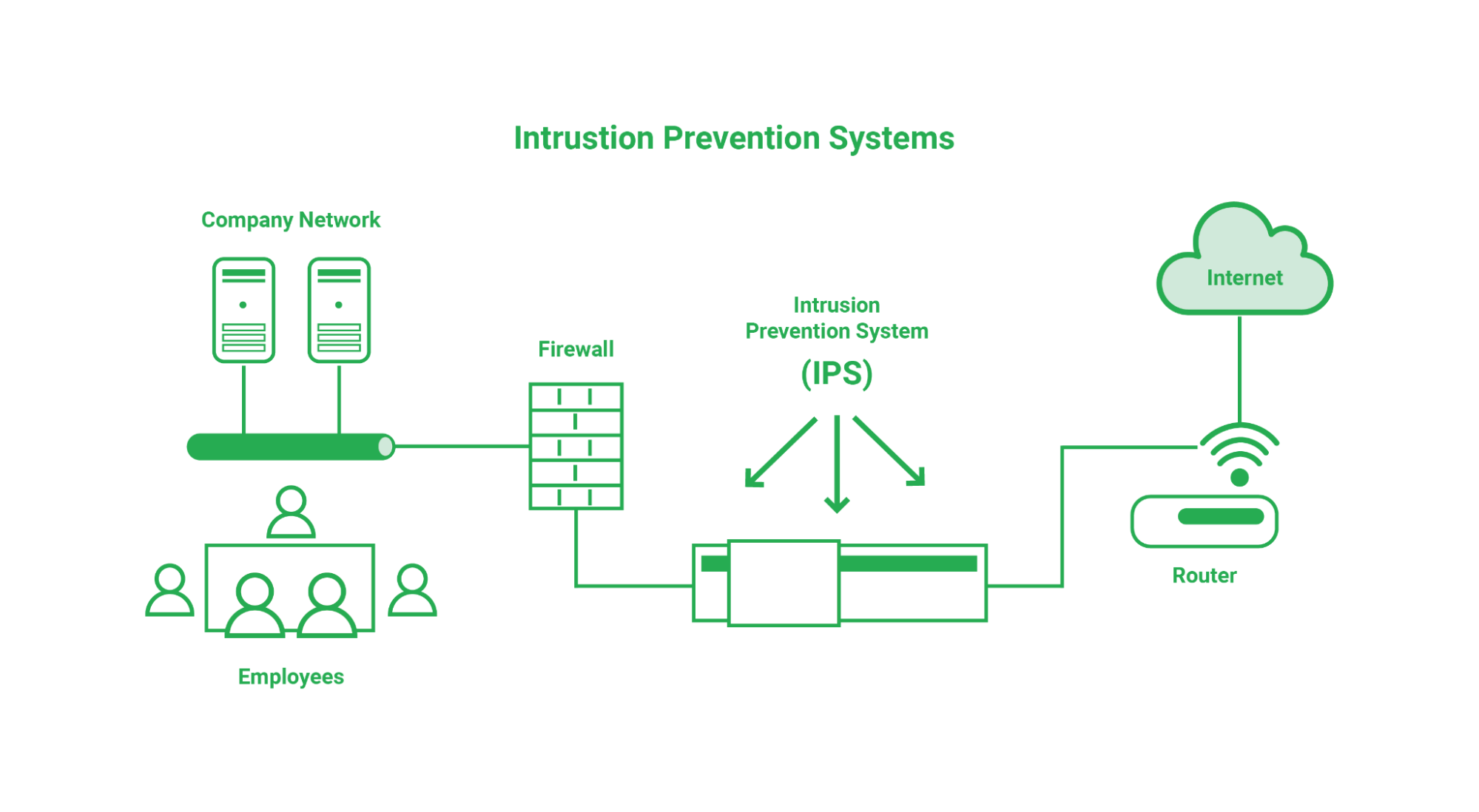
Intrusion Prevention System (IPS)
An intrusion prevention system (IPS), sometimes known as an intrusion detection and prevention system (IDPS), is a technology that monitors a network for harmful actions such as attempts to exploit a known vulnerability.
The fundamental function of an Intrusion Prevention System is to detect any suspicious activity and either allow (IDS) or prevent (IPS) the danger. The attempt is recorded and reported to network administrators or Security Operations Center (SOC) personnel.
Brute force assaults, Denial of Service (DoS) attacks, and vulnerability exploits are all examples of network security attacks that IPS technology can identify and avoid. A vulnerability in a software system is a flaw, and an exploit is an attack that takes use of that flaw to obtain control of the system. When a vulnerability is reported, attackers frequently have a window of opportunity to exploit it before a security remedy is implemented. In these situations, an Intrusion Prevention System (IPS) can be utilized to immediately stop the attacks.
To come up with the best solution for threats mentioned above we can use Identity and Access Management (IAM) for unauthorized access or intrusion from the attackers.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is the process of defining and managing the roles and access privileges of individual network users and the circumstances under which users are granted (or denied) privileges. These users can be customers (customer identity management) or employees (employee identity management). The central goal of the IAM system is the digital identity per individual.
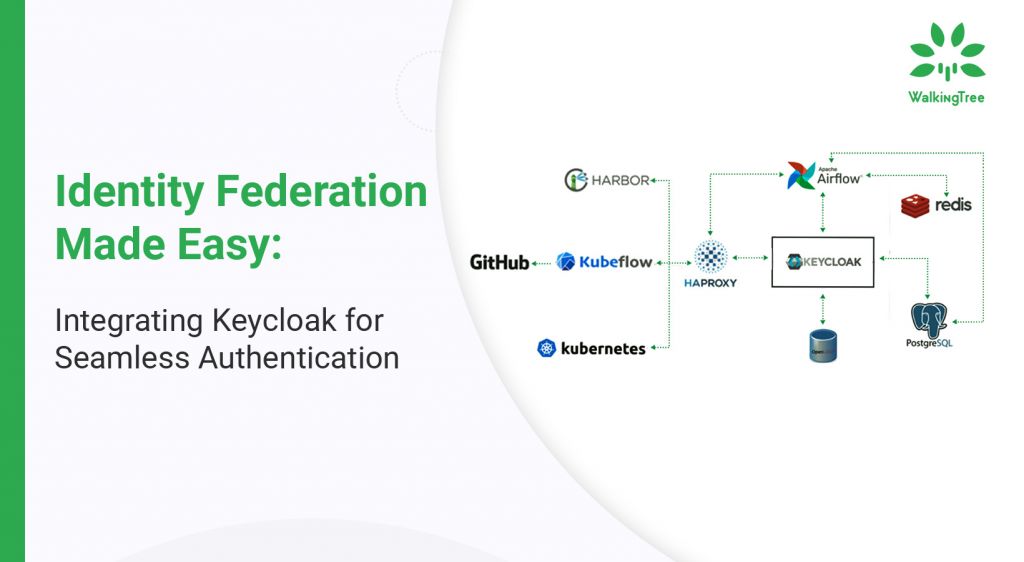
Identity is becoming a new boundary, and these IAM tools have evolved to help organizations protect their assets as they move less to rely on traditional boundary defenses and move into a zero-trust environment. There is a great tool called Keycloak to overcome the identity threat.
Keycloak
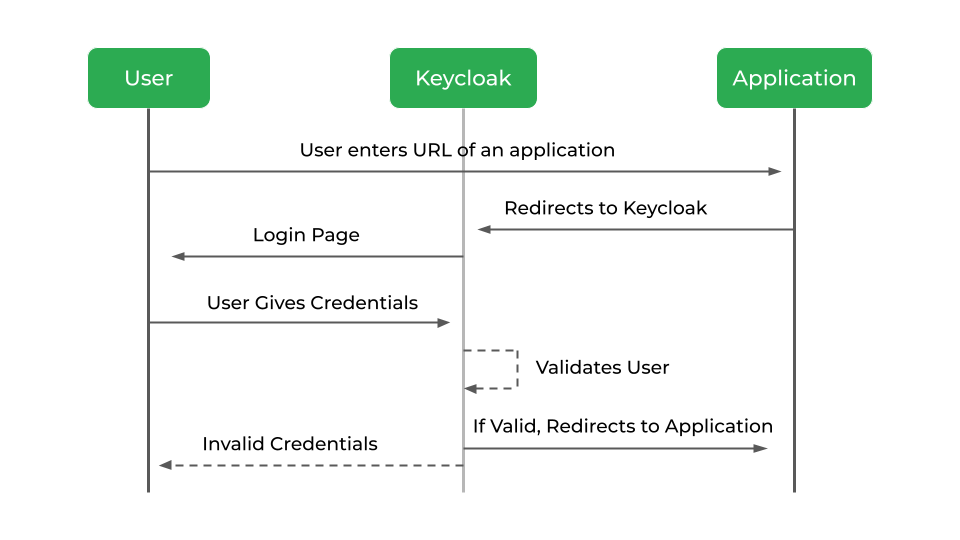
Keycloak: A modern application, service-oriented open source Identity and Access Management system. It makes it simple to protect apps and services with little to no code, requiring only the configuration of functions rather than the writing of code. As a result, it will reduce development time.

Keycloak can help you with
- Authorization & Authentication. Log in to the system using a single account or a single virtual identity.
- Identity Brokering. Validation of the identity between different services via OpenID Connect or SAML 2.0 IdPs.
- LDAP & Active Directory.
- Security.
- Up-to-date.
- Performance.
- Active Community.
- Scalability.
- Open Source
How Keycloak Works
Application Security Testing Tools
There are three main categories of tools in the AppSec toolset: SAST, DAST, and IAST.
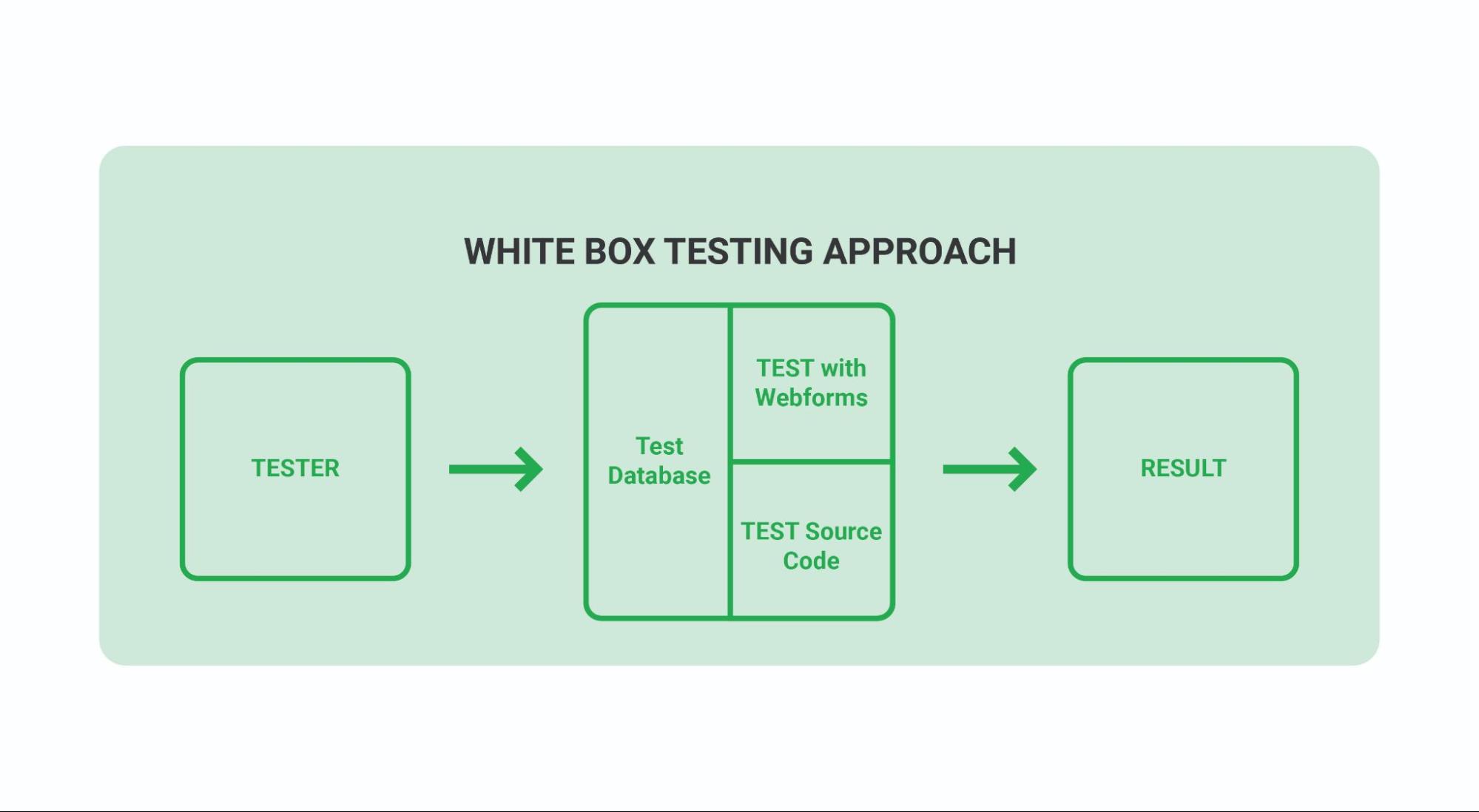
SAST: Static Application Security Testing, sometimes referred to as “white box testing,” is a method of software security vulnerability testing. The tool analyzes the source code as the application is developed to detect and report weaknesses that can lead to security vulnerabilities. This type of tool can help you identify security vulnerabilities at an early stage of development.
SAST analysis help identify issues like:
- Race conditions
- Traversals of paths
- Input validation is not present.
- Errors in numbers or data types
- Untrustworthy references or points
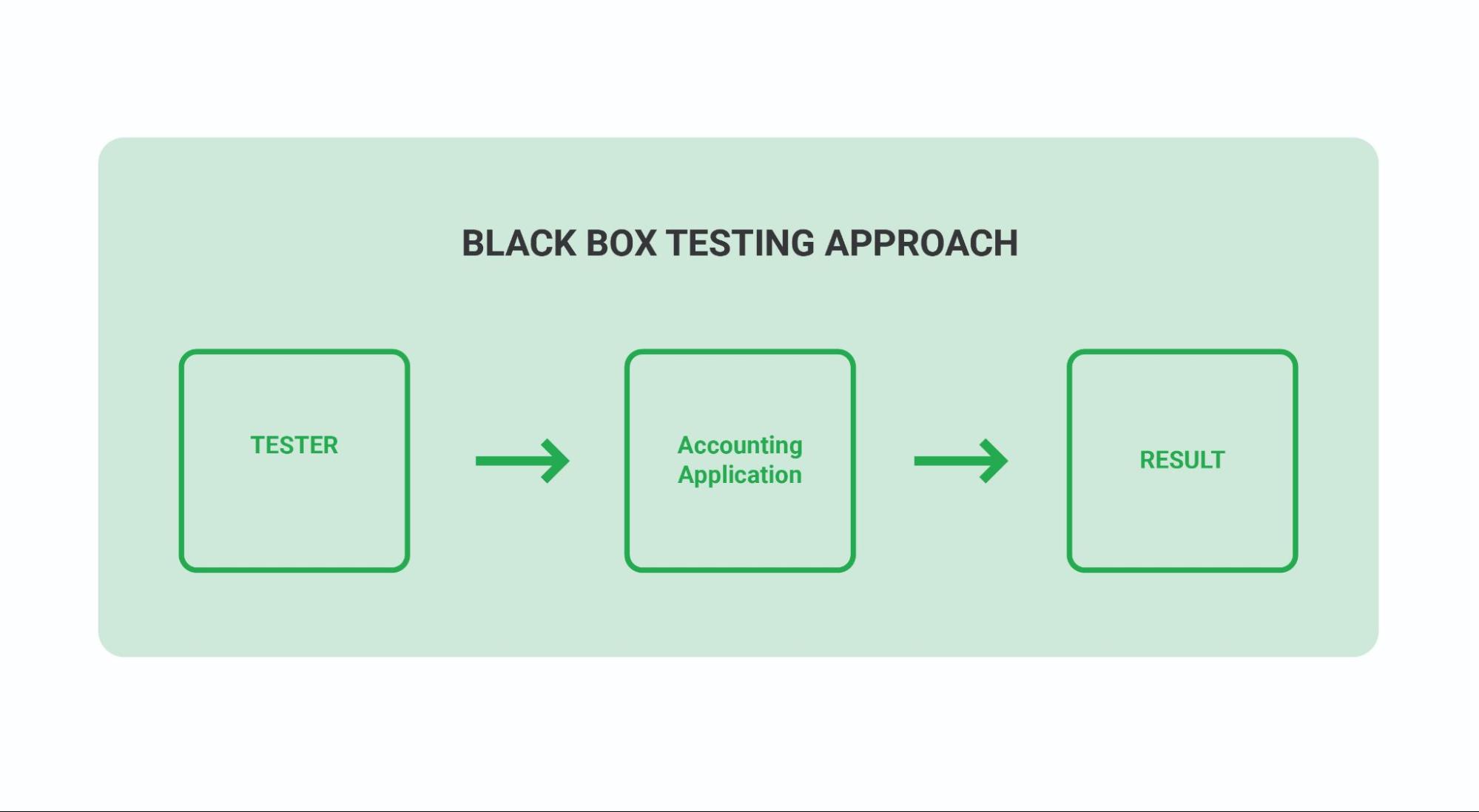
DAST – Dynamic Application Security Testing, commonly referred to as “black box testing,” is a sort of software security vulnerability test. This type of tool detects conditions that indicate security vulnerabilities of source code while it is running. This type of tool can help you identify security bugs, runtime issues, and environment-related issues in the development cycle.
DAST can detect indicate security vulnerabilities like:
- Interfaces that are insecure or vulnerable
- Unusual requests and reactions
- Issues with scripting in languages such as JavaScript and Python
- Injection of data or code
- Anomalies in sessions
- Issues with authentication
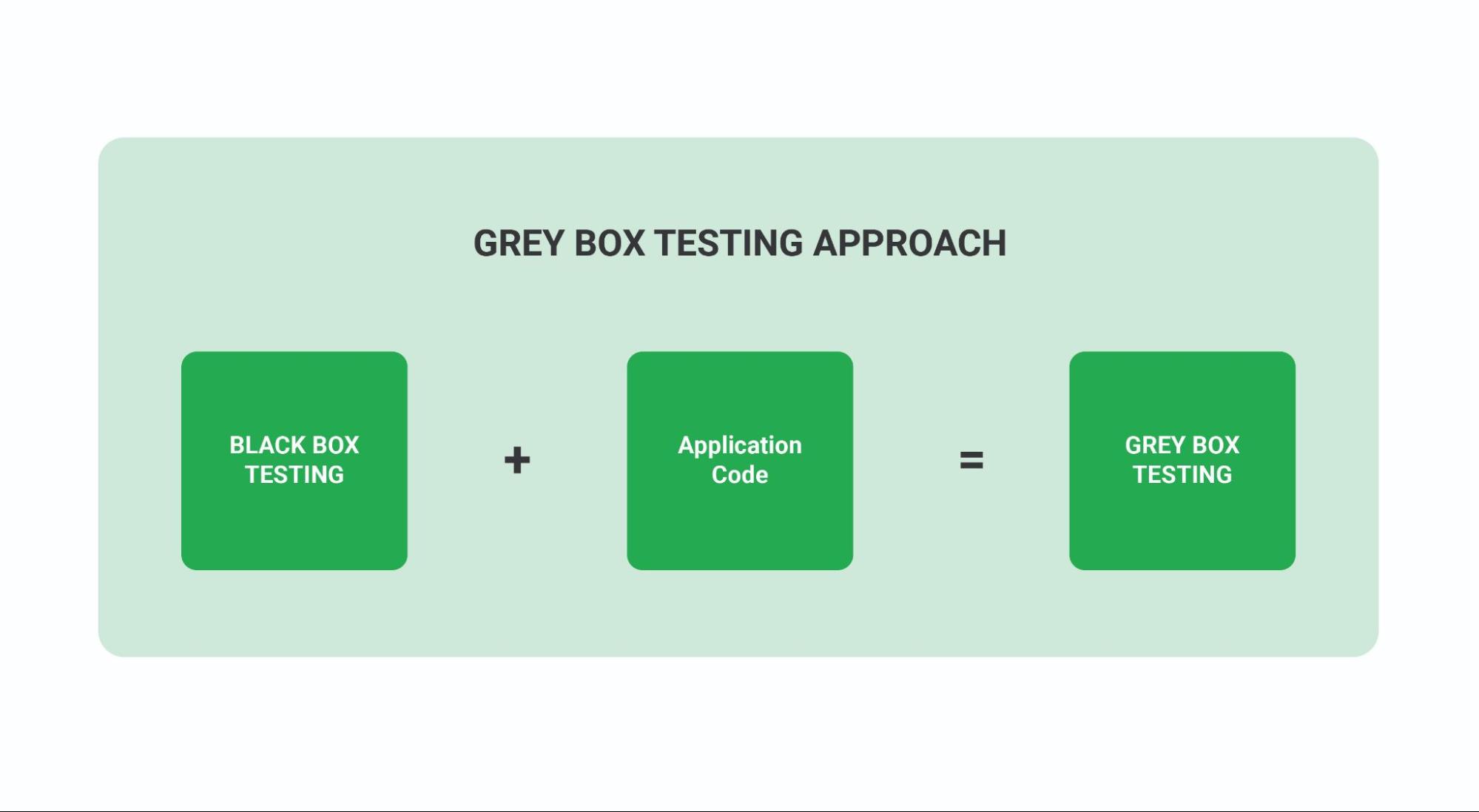
IAST – Interactive Application Security Testing (IAST), also known as “Gray box testing“, is a hybrid approach combining SAST and DAST. Our interactive approach to security testing combines static and dynamic analysis to identify known vulnerabilities and verify that they can be used and exploited in a running application.
The IAST tool can collect detailed information about application execution flow and data flow and simulate complex attack patterns. You can perform a live scan of a running application to test the application’s response and adjust the tests accordingly. This can be used to automatically create new test cases, etc.
This approach reduces the number of false positives by allowing IAST tools to delve deeper into suspected security issues. It also makes for a much more natural fit into the agile development process with quick releases.
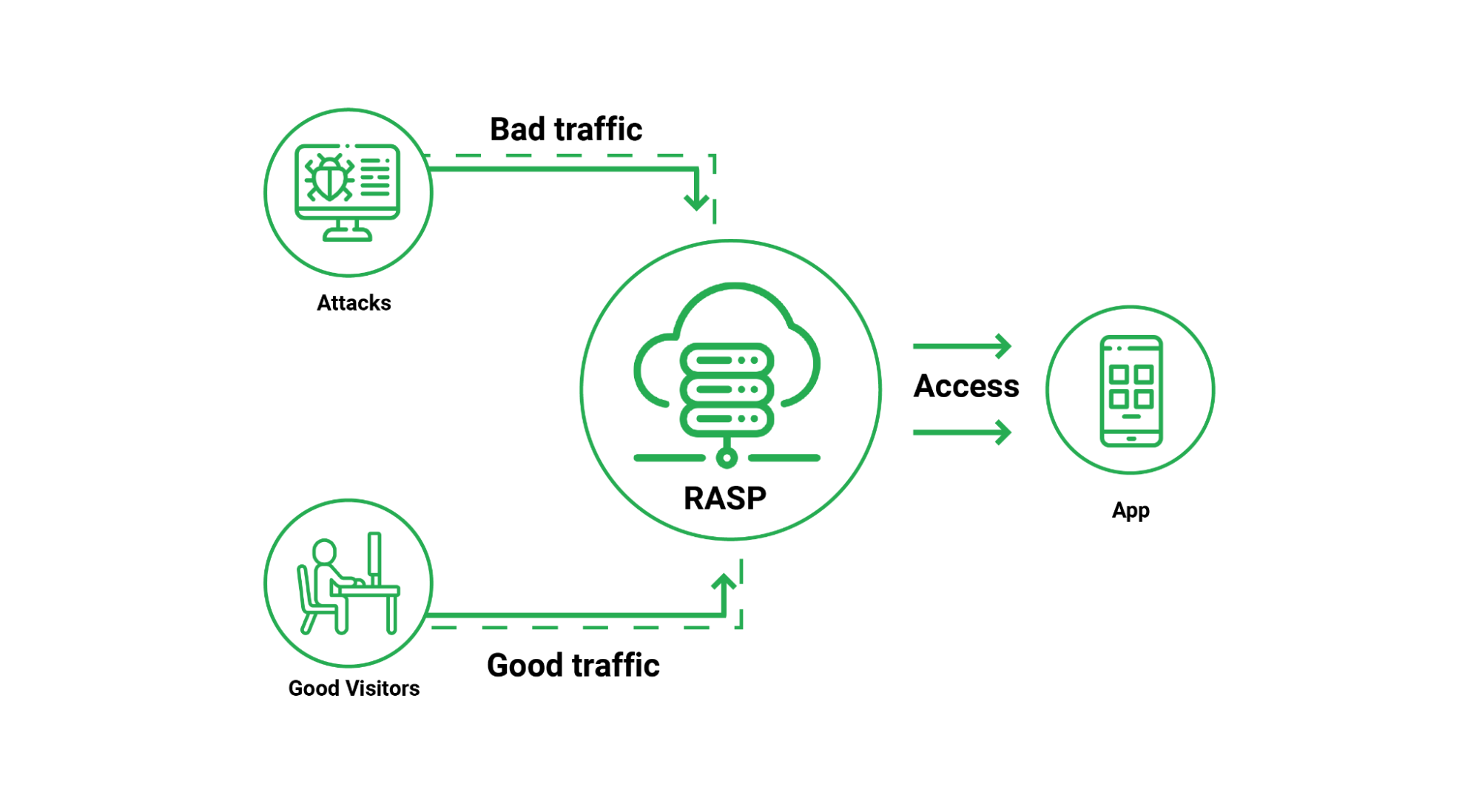
What Is Runtime Application Self-Protection (RASP)?
Runtime Application Self Protection (RASP) is a security solution designed to provide personalized application protection. It uses information about your application’s internal data and state to detect runtime threats that other security solutions might miss or overlook.
How Does RASP Work?
RASP addresses and protects specific applications rather than generic security solutions at the network or endpoint level. This more targeted deployment location allows RASP to track the input, output, and internal state of the protected application. By deploying RASP, developers can identify vulnerabilities in their applications. RASP solutions can also block attempts to exploit existing vulnerabilities in deployed applications.
The RASP’s targeted monitoring can detect a wide range of threats, including zero-day attacks. Because RAPS has an idea on an internal goal of an application, you can detect changes in behavioral changes that can be caused by a new attack. This allows you to respond to Zeroday attacks based on what affects the target application.
Benefits of Runtime Application Self-Protection (RASP)
1. Contextual Awareness – When the RASP solution identifies a potential threat, it receives additional contextual information about the current state of the application and the data and code affected. This context can be very useful for investigating, sorting, and fixing potential vulnerabilities because it indicates exactly where in your code the vulnerabilities are and how they can be exploited.
2. Layer Attacks – As RASP integrates with specific applications, it provides deep application-layer visibility. At the application level, this visibility, insights and knowledge can help uncover a wider range of potential attacks and vulnerabilities.
3. Zero-Day Protection – RASP can use signatures to identify attacks, but it is not limited to signature-based detection. By identifying and responding to anomalous behavior within protected applications, RASP can detect and block even zero-day attacks.
4. Lower False Positives – RASP has deep understanding of application internals, including the ability to see how a potential attack affects application performance. This greatly increases RASP’s ability to distinguish between real attacks (which have a real negative impact on application performance and security) and false positives (such as SQL insert attempts are never included in the SQL query). Reducing this number of false positives eases the burden on security teams and allows them to focus on real threats.
5. Lower CapEx and OpEx – RASP is designed to be easy to deploy and can make a significant difference in application vulnerability and false positive rates. This combination reduces both upfront costs (CapEx) and effective application protection costs (OpEx) compared to manual patches and web application firewalls (WAFs).
6. Easy Maintenance – RASP works based on preview of an application, not based on traffic rules, learning or blacklisting. SOC teams appreciate this reliability, and CISOs appreciate resource savings. Applications become self-protected and protected wherever they are.
7. Flexible Deployment – While RASP is generally based on HTML standards, its API can be easily adapted to work with different standards and application architectures. This allows it to protect even non-web applications that use standards like XML and RPC.
8. Cloud Support – RASP is designed to be integrated and deployed as part of the application it protects. This allows it to be deployed anywhere protected applications can run, including the cloud.
9. DevSecOps Support – RASP solutions are designed for integration into DevOps continuous deployment and integration (CI/CD) systems. This makes it easier to deploy RASP and support DevSecOps operations.
Runtime Application Self-Protection (RASP) Use Cases
Web Application Protection: Web applications and APIs are an important part of an organization’s infrastructure, but can be vulnerable to a wide range of attacks. These applications are exposed to the public internet and are often subject to exploitable vulnerabilities. By implementing RASP to protect these applications and APIs, an organization can limit the cybersecurity risks and attack surface of its web infrastructure.
Cloud Application Protection: Securing the cloud can be complicated because applications run on leased infrastructure outside the perimeter of the organization’s network. Integrating RASP into these applications provides them with a high level of security in a portable and largely infrastructure-independent form.
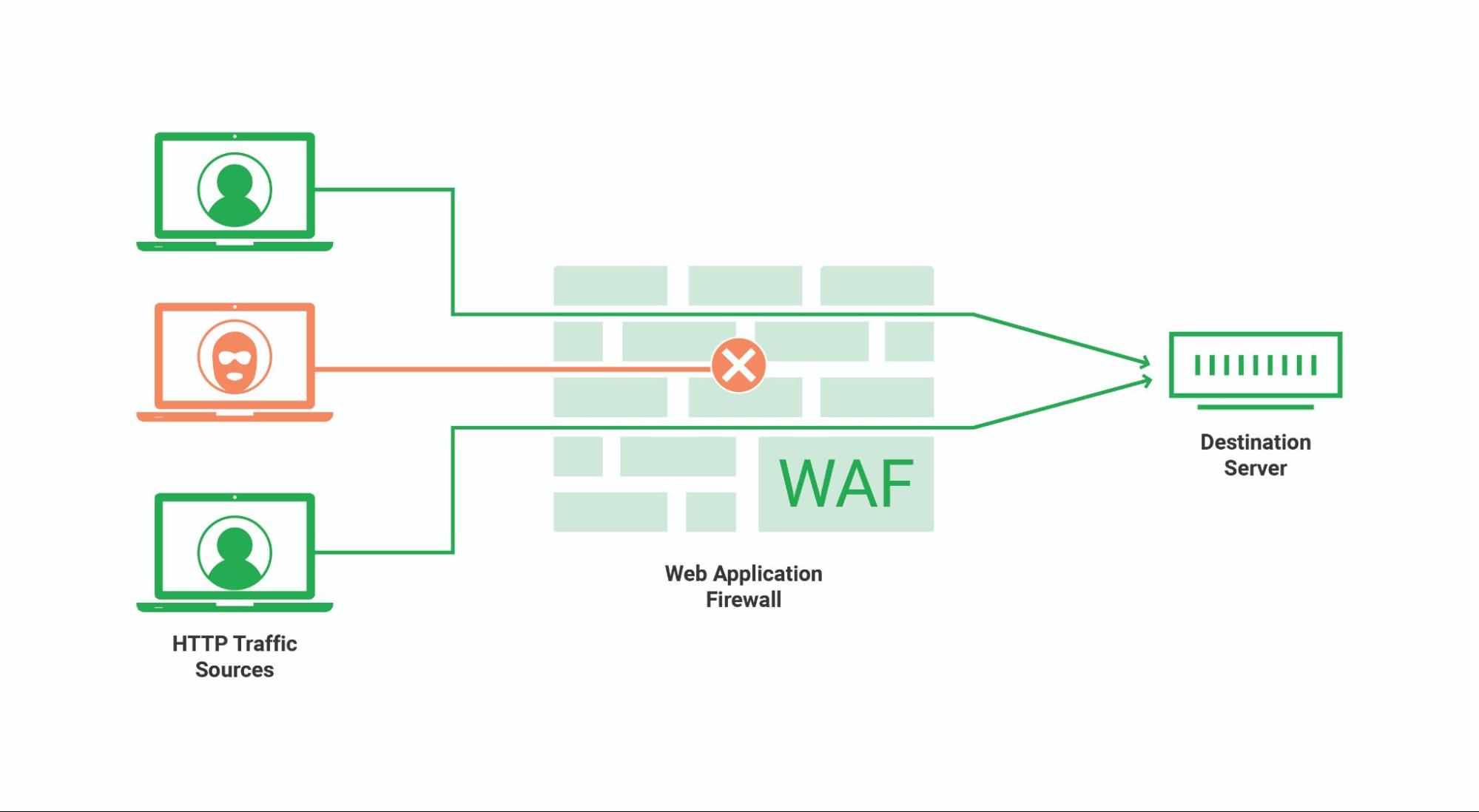
Web Application Firewall
A web application firewall (WAF) is deployed at the edge of the network to inspect to and fro web application traffic. You can filter and monitor traffic to protect against attacks such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
WAF operates at network layer 7 (application layer). It can protect against a wide range of application-layer attacks, but it cannot operate on its own and must be combined with other security tools to protect against attacks on other network layers or other parts of the security environment.
How RASP and WAF Complement Each Other
Runtime Application Self-Defense and Web Application Firewall (WAF) are two complementary solutions for application security. While WAF provides a first line of defense, filtering many web application threats before they reach the target application, RASP uses the context provided by deep visibility into these applications to identify Identify and block attacks that escape the web application firewall. This combination minimizes the impact of vulnerable attacks while providing protection against more sophisticated threats.
Appsec Importance in Devops
AppSec is essential at every stage of the software development process. AppSec operations, on the other hand, are frequently postponed until the very end of the project, right before the application is released. If security flaws are identified late in the development process, remediation can be time-consuming and costly. AppSec deficiency in DevOps processes can also expose consumer data. To avoid this, AppSec activities must be integrated into every aspect of the DevOps process, ensuring that your applications are secure from the start.
Putting these best security strategies to work in your enterprise.
It takes collaborative team efforts to maintain a secure application. It can take months, but you can start immediately by creating a blueprint for all your applications and a roadmap to securing them in the next year or so.
The right foundation for a secure application focuses on three things:
- Finding out he vulnerabilities before the attackers
- Fixing these vulnerabilities to prevent hacking attempts
- Continuous monitoring to collect data for visibility, security intelligence, and DDoS patterns
If you have any questions about securing your applications, our analysts would love to help. Drop in a line on connect@walkingtree.tech, and one of our techs will get back to you!