Keycloak and Multi-Factor Authentication (MFA): Strengthening Security Layers
Multi-Factor Authentication (MFA) emerges as a powerful solution, offering an additional layer of security that goes beyond passwords. Securing online identities and data has become a paramount concern nowadays. Traditional password-based authentication methods are becoming increasingly vulnerable to the ever-evolving threats in cyberspace. This is where Multi-Factor Authentication (MFA) significantly reduces the risk of unauthorized access, even if one factor is compromised
|Understanding Multi-Factor Authentication
Multi-factor authentication operates on the principle of “something you know, something you have, and something you are.” This multi-layered defense approach significantly adds complexity beyond traditional password-based authentication, making it exponentially more challenging for unauthorized entities to gain access.
Common Multi-Factor Authentication Methods
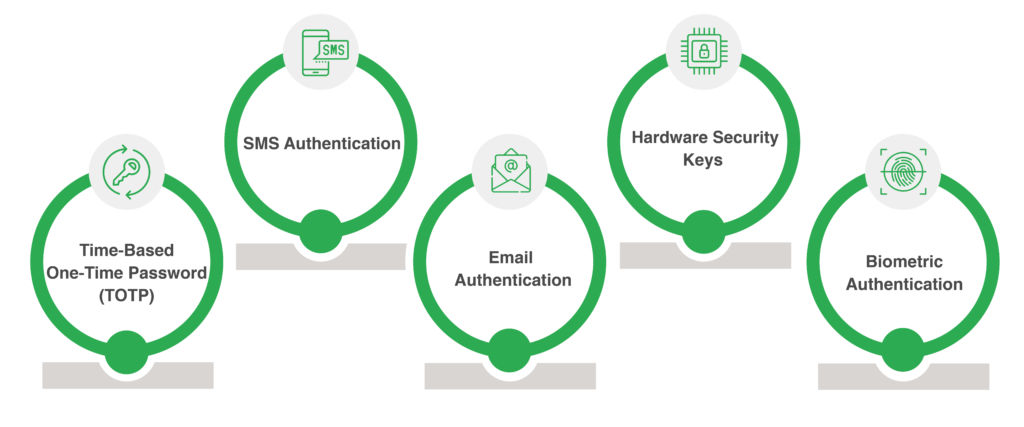
To comprehend the significance of Multi-Factor Authentication, it’s crucial to explore common Multi-Factor Authentication methods:
- Time-Based One-Time Password (TOTP): This approach utilizes short-lived codes (typically 6 digits) valid for a limited time (30-60 seconds). These codes can be stored in password managers or dedicated authenticator apps like Google Authenticator, offering convenient and secure access.
- SMS Authentication: Prioritizing user experience, this method sends a one-time code directly to the user’s phone for verification. While convenient, it is susceptible to SIM swapping attacks, necessitating additional security measures.
- Email Authentication: Similar to SMS, email authentication delivers a one-time code to the user’s email address. However, it carries the inherent risk associated with email security, necessitating strong passwords and vigilant monitoring.
- Hardware Security Keys: For those seeking the highest level of security, hardware security keys offer an ideal solution. These physical tokens require physical possession for authentication, adding an extra layer of protection beyond digital verification.
- Biometric Authentication: By leveraging unique biometric identifiers such as fingerprints or iris patterns, this method offers an unparalleled level of security. While requiring specific hardware support, it provides a highly secure and user-friendly authentication experience.
|Keycloak’s Multi-Factor Authentication Capabilities
A Powerhouse for Secure Authentication
Keycloak stands out as an open-source Identity and Access Management solution that simplifies the implementation of Multi-Factor Authentication. It seamlessly integrates with various applications, empowering organizations to enforce Multi-Factor Authentication for secure access to critical resources. Keycloak’s robust features, including user management and role-based access control, make it a powerhouse for secure authentication.
Native Support for Diverse Multi-Factor Authentication Methods
Keycloak’s native support for diverse Multi-Factor Authentication methods sets it apart. From traditional SMS authentication to the advanced security afforded by authenticator apps (TOTP and HOTP) and biometric integration, Keycloak offers a comprehensive suite of options. This flexibility ensures that organizations can choose the MFA methods that align best with their security and user experience requirements.
|Bringing Control and Visibility to Quality Assessment
By leveraging custom evaluators that can be tailored as per project requirements and objectives, Langsmith ensures optimum control and visibility of the quality assessment process. By doing away with a one-size-fits-all approach custom evaluators of Langsmith can offer a detailed and nuanced analysis of a solution.
1. Encompassing a varied range of criteria
The custom evaluators of Langsmith encompass a wider range of criteria for defining the scope and metrics of testing. Thanks to this ability to accommodate diverse criteria, specific testing requirements and corresponding expectations for any project can be easily defined irrespective of the complexity and size of a solution. Through this, we can evaluate the coverage
2. Granular view of test results
By presenting an overview of the evaluation results, offers a clearer insight into areas that require improvement or where the script coverage may have overlooked certain points. This visibility is crucial for enhancing the overall quality of the project by pinpointing specific areas that need attention or refinement. It acts as a valuable feedback mechanism, guiding testers to focus their efforts on addressing identified shortcomings and ensuring comprehensive coverage in subsequent iterations of the project.
3. Actionable presentation of test results
Last but not least, Langsmith also presents its test results through neatly presented reports that instantly offer actionable insights into different evaluation areas. The detailed and easily digestible test reports facilitate effective decision-making for QA teams and stakeholders of the project staging up further improvements in running tests.
|Advantages of Multi-Factor Authentication in Keycloak
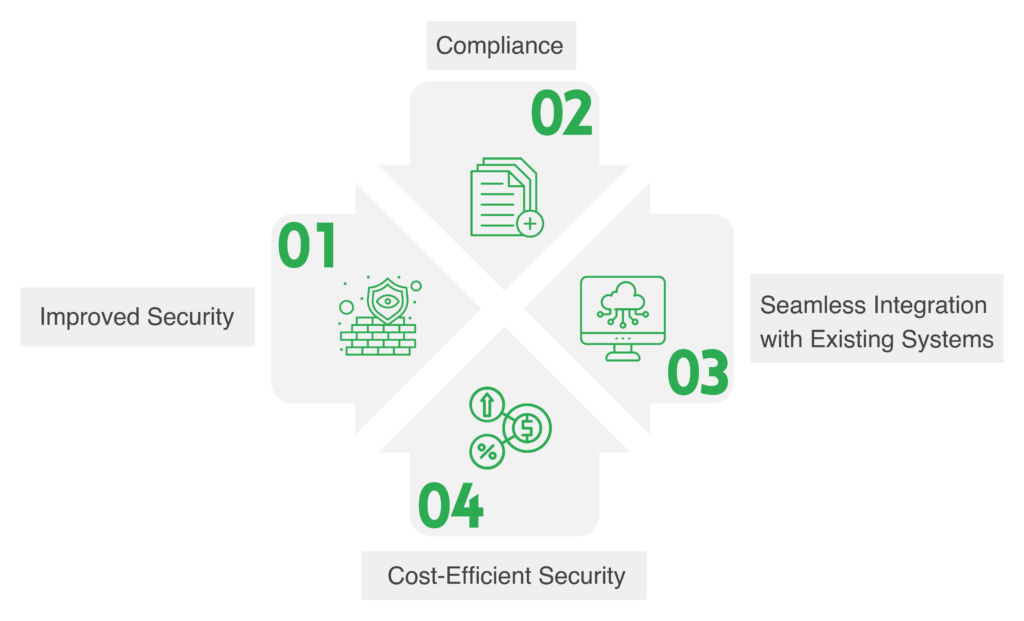
- Improved Security: The primary advantage of implementing Multi-Factor Authentication with Keycloak is the substantial improvement in security. By requiring multiple factors for authentication, the risks associated with password-only authentication are mitigated. Even if one factor is compromised, unauthorized access remains highly unlikely, enhancing the overall security posture.
- Compliance: In an era where regulatory compliance is non-negotiable, Multi-Factor Authentication implementation becomes crucial. Keycloak’s MFA capabilities align with various compliance standards and regulations, ensuring that organizations meet the necessary requirements for data protection and user authentication.
- Seamless Integration with Existing Systems: Keycloak is designed for seamless integration with existing systems and applications. This makes the implementation of Multi-Factor Authentication straightforward, without disrupting established workflows or user experiences.
- Cost-Efficient Security: While providing robust security, Keycloak’s Multi-Factor Authentication is a cost-efficient solution. It minimizes the potential financial losses associated with security breaches and data compromises, making it a strategic investment for organizations.
|Setting Up Keycloak for Multi-Factor Authentication
Strategic Configuration Steps
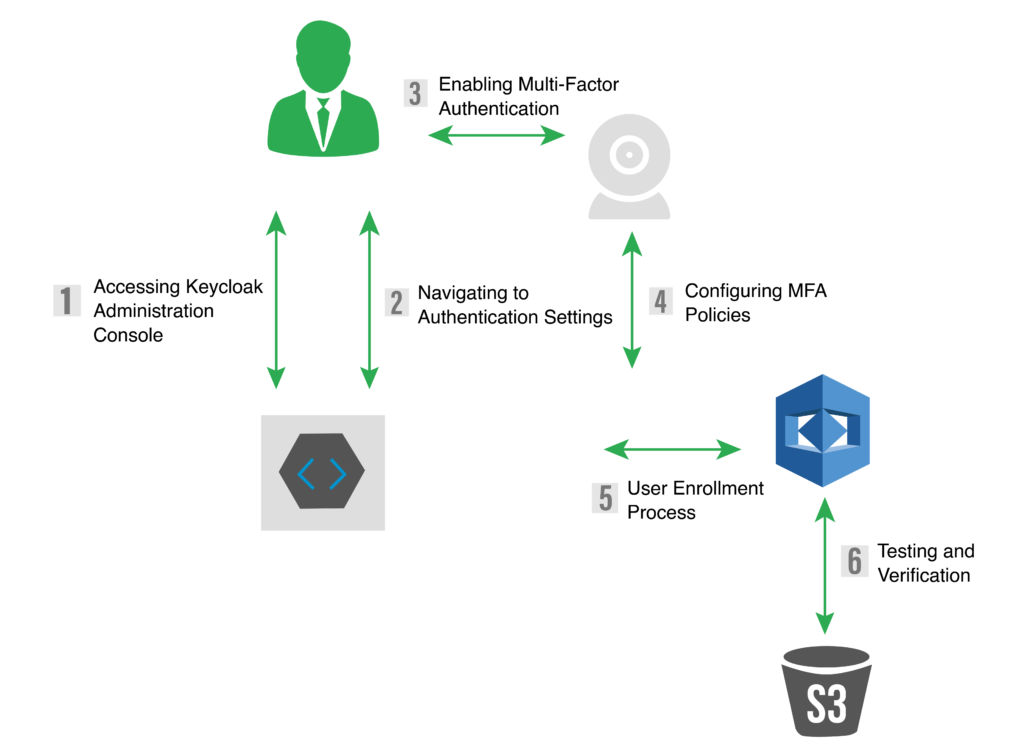
Implementing Multi-Factor Authentication with Keycloak involves strategic configuration steps to ensure a seamless and secure process. The following steps guide administrators through the setup:
- Accessing Keycloak Administration Console: Log in with administrator credentials to gain access to the Administration Console, the central hub for configuring authentication settings.
- Navigating to Authentication Settings: Within the Administration Console, navigate to the Authentication settings section, where a range of authentication-related configurations is available.
- Enabling Multi-Factor Authentication: Enable Multi-Factor Authentication for the desired realm or client, choosing from methods such as TOTP, HOTP, SMS, or biometric authentication based on organizational security requirements.
- Configuring MFA Policies: Define Multi-Factor Authentication policies based on security requirements, taking into consideration conditions, user roles, and temporal policies. This step ensures that MFA is applied contextually and meets specific organizational needs.
- User Enrollment Process: Guide users through a user-friendly Multi-Factor Authentication enrollment process. An intuitive and user-friendly onboarding experience is crucial for encouraging widespread adoption among end-users.
- Testing and Verification: Before deploying Multi-Factor Authentication in a production environment, thorough testing is essential. Keycloak provides the necessary tools to verify the effectiveness and user experience of the configured Multi-Factor Authentication methods.
|Multi-Factor Authentication and Application Security
Strengthening Overall Application Security
Multi-factor authentication significantly strengthens application security, especially in scenarios involving privileged access or sensitive data transactions. Password-based risks are mitigated, and the additional layers of authentication contribute to a robust defense against unauthorized access attempts.
|Multi-Factor Authentication Auditing and Monitoring with Keycloak
Crucial for Security Compliance
Implementing robust monitoring and auditing of Multi-Factor Authentication (MFA) events is crucial for security compliance. Keycloak offers features for setting up auditing and monitoring to track Multi-Factor Authentication activities in real time. This proactive approach ensures that any anomalies or suspicious activities are detected promptly, contributing to a more secure IAM environment.
|Real-world use cases across Industries
Keycloak’s Multi-Factor Authentication (MFA) extends its security capabilities across diverse sectors. In the financial realm, it fortifies transactions with layers like SMS codes and biometrics, minimizing unauthorized access risks. In healthcare, it ensures secure access to sensitive patient records, adhering to data protection regulations. Government systems benefit from its robust MFA methods, creating a resilient defense against unauthorized entry. E-commerce transactions are shielded with SMS authentication and authenticator apps, securing customer accounts and mitigating fraud.
Keycloak safeguards cloud infrastructure, protecting confidential data and communication channels. Educational institutions leverage its Multi-Factor Authentication to enhance data security, fostering a secure digital learning environment. Telecommunications providers utilize Keycloak’s Multi-Factor Authentication (MFA) to ensure secure user authentication, protecting mobile accounts and communication channels. In the manufacturing industry, Keycloak’s MFA enhances security by ensuring only authorized personnel access and control critical systems, preventing interference.
Keycloak even secures logistics and supply chain systems with an extra layer of protection through methods like SMS authentication, safeguarding sensitive information. Finally, within technology research and development, Keycloak’s Multi-Factor Authentication fortifies intellectual property and research data, ensuring confidentiality and safeguarding proprietary technologies from unauthorized access.
|Keycloak’s Multi-Factor Authentication for a Robust Future
Embracing security with confidence involves prioritizing Multi-Factor Authentication with Keycloak. The combination of Keycloak’s robust capabilities and the strategic implementation of Multi-Factor Authentication provides organizations with a powerful tool to navigate the cybersecurity landscape. Achieving a balance between security, compliance, and user experience is paramount in a world where digital resilience is of utmost importance. By adopting Multi-Factor Authentication with Keycloak, organizations can not only comply with industry standards but also enhance their overall security posture, ultimately empowering them to navigate the challenges of the digital era confidently.
Contact us to learn more about Keycloak’s Multi-Factor Authentication solution and fortify your digital fortress.