Avoiding API failures like a ninja – A definitive guide


APIs have been around at an operational level since the time personal computers have existed. Private APIs are used within organizations to share data and integrate systems internally. A well-written API allows developers to make minor changes without incurring the costly expenditures of new software.
However, API failures can be devastating. In 2012, GoDaddy’s DNS look-up failure caused millions of DNS names to be unreachable.
A significant number of SaaS providers use Amazon’s AWS. They guarantee an EC2 uptime of 99.95%. However, what can happen during the 0.05% period was witnessed in 2011 when Amazon’s US-East availability zone failed and a major disruption was caused by the unavailability of a majority of the systems hosted there.
There are multiple such cases where API failures have caused significant damage. The only way to ensure these failures do not happen frequently and minimize the damage is by following the best practices.
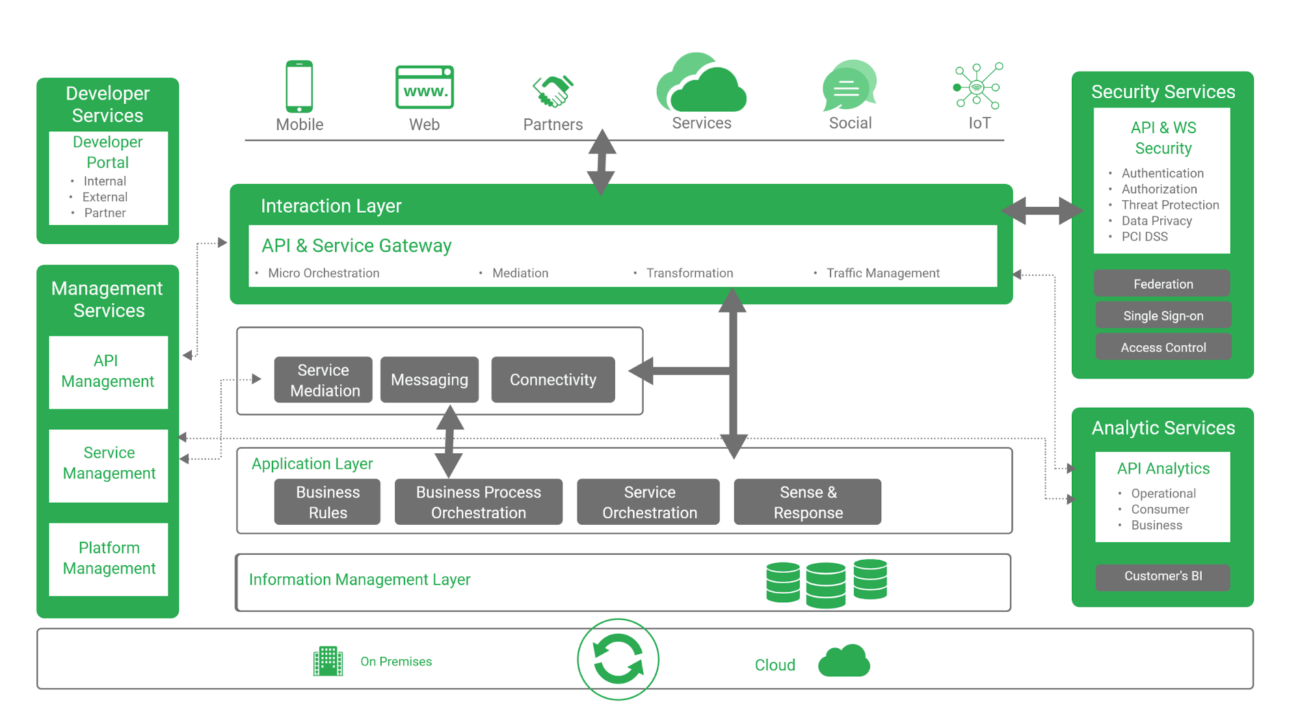
Top Best Practices in API development
1. Clear and Concise Documentation
Documents are often automatically generated according to the API definition. If the documentation is created by developers, it should be easy to understand for the experienced and amateurs alike.
Complete documentation is required to familiarize users with security, authentication, and fault management. In addition, it provides compelling tutorials, guides, and easy-to-use resources. Comprehensive documentation makes it easy for users to use the API.
2. Utilizing JSON as a Data Format
JSON is the most commonly used data format, although data can be sent in other formats such as CSV, XML, and HTML. JSON syntax can make data easy for humans to read. It is easy to use and provides quick and easy data evaluation and execution. Moreover, it contains a wide range of compatible supported browsers.
3. API Versioning
This practice allows developers to make changes to specific actions or data structures. You can address multiple API versions as your project grows over time and scale. But the advantage is that it allows developers to make more improvements and changes in their service while retaining a portion of API users that are slow to accept new changes or not ready for changes.
We received mixed feedback on whether we should include the API version in the URL or the header. Academically, it should be in the title. But the version must be in the REST API URL. This ensures that the browser is searchable in different versions, providing a seamless and easy development experience.
An API is generally unstable and subject to change. While you can’t avoid change, you should look at ways to manage change. Scheduling a well-documented and monthly-reported shutdown is a good practice for many APIs.
4. Error Management
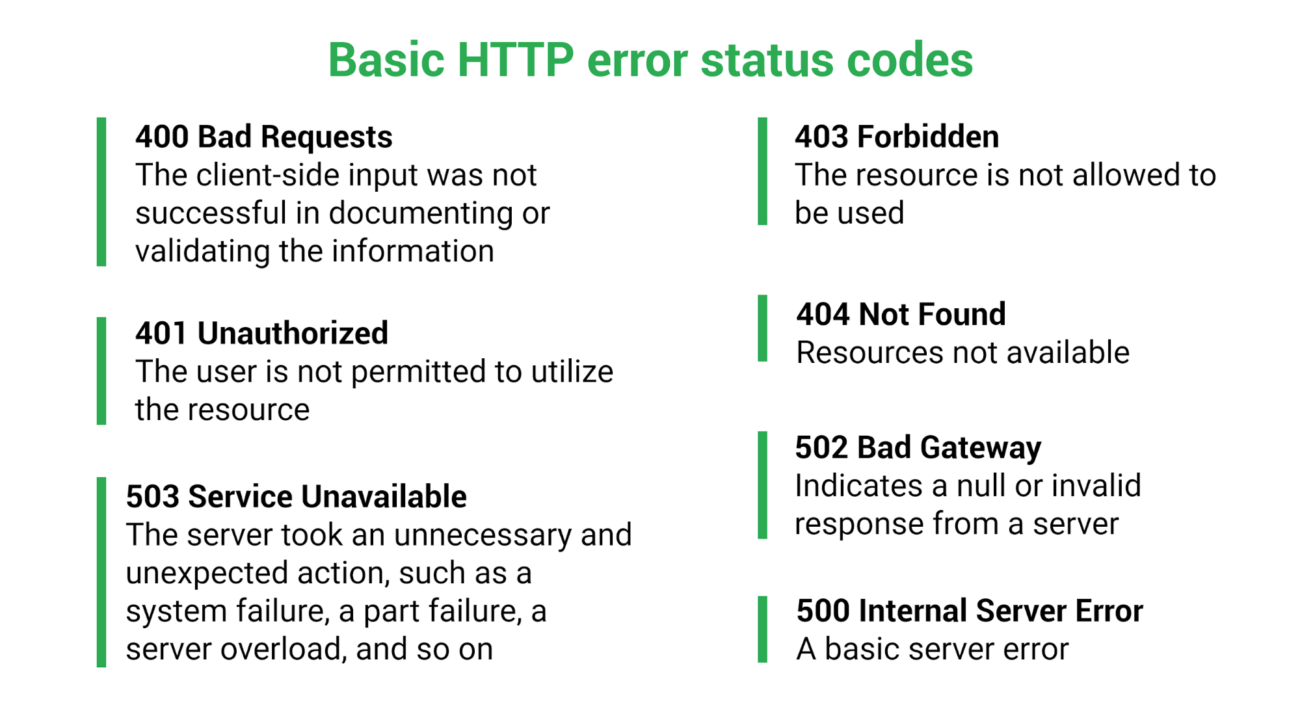
Errors must be handled intelligently to reduce confusion for all API users. This returns an HTTP response code explaining the nature of the error that occurred. The API maintainers pull a lot of data from it to assess the source and reason of the problem.
If you want to keep your systems error-free, leave them unmanaged. Therefore, the API client must handle the error. Here are some basic HTTP error status codes:
5. Enhancing API Security
While cybersecurity is a vast topic that involves all internet technologies, APIs present unique challenges because they sit between third-party developers and a company’s resources. Because a compromised endpoint offers direct access to sensitive information, successful API security breaches can be highly destructive to an organization and its users.
It’s difficult to overestimate the impact of a successful attack. While the financial consequences can be significant, the harm to your brand may be irreversible. You’ll almost certainly lose customer trust and credibility, as well as that of the organizations who use your API. By extension, third-party integrated apps may be damaged.
Types of API Attacks
We need to know what we’re up against before we go over the best practices for hardening your API. The following are the most prevalent API exploits that you should be aware of:
Stolen Authentication
Taking the identity of an authorized user is one of the simplest ways to gain access to an API. If an authentication token, for example, slips into the wrong hands, it might be exploited to gain access to resources with malevolent intent while looking to be legitimate. To get access, cybercriminals will try to guess authentication credentials or break a poor authentication procedure.
Man-in-the-Middle Attack
When a hacker intercepts an API request or response between an end-user and an API, this is known as a man-in-the-middle (MITM) attack. They may steal the communication’s sensitive data (such as account login credentials or payment information) or alter the request/message.
Code Injections
Code injection, in which an attacker sends a script to the application’s server via an API request, can also occur with APIs with authentication and validation vulnerabilities. This script is designed to reveal or delete data, provide false information and/or cause damage to internal application components. The term “SQL injection” will also appear., which refers to injecting code into an SQL database.
Denial-of-Service Attack
Denial-of-service (DoS) attacks flood a server’s resources with API requests, causing it to slow down, break, or crash. These attacks are frequently launched concurrently from numerous malicious sources, resulting in a distributed denial-of-service (DDoS) attack.
APIs aren’t going away anytime soon, despite these dangers. Almost any online service that wants to integrate with others will require one or more APIs, and each new web API creates a new potential for hackers to steal personal information. As a result, everybody in charge of a software integration should be aware of API-specific security procedures.
Securing your APIs – all that you need to do
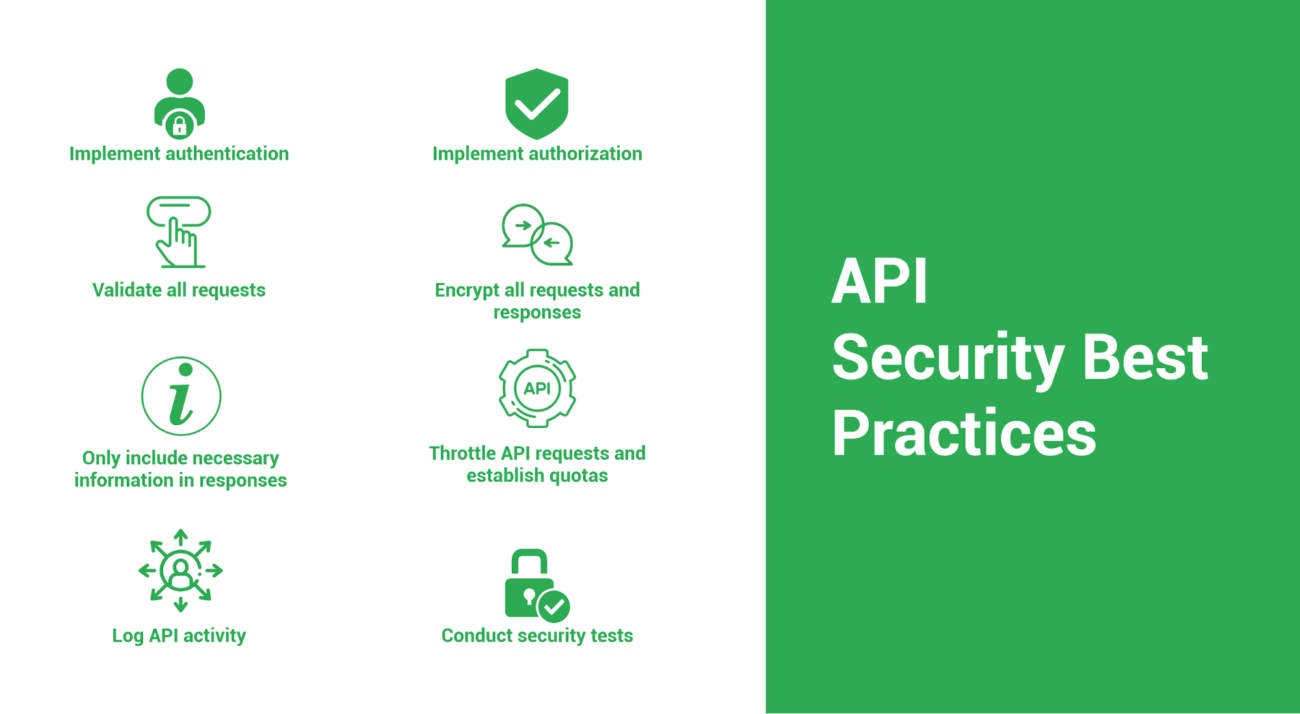
While any firm with an API might be attacked, APIs — and API security — are implemented differently by each. An API that allows payment information to be accessed requires greater security than, say, an image-sharing service.
As a result, the following pointers are generic and can be applied to any application that uses a REST API. REST APIs employ the same Hypertext Convey Protocol (HTTP) that is used to transmit HTML documents to browsers to transfer data (which we see as websites). Many public APIs and internal APIs use this style of architecture (used in microservices, for example). REST APIs are used by a number of modern apps, including Netflix, Uber, and Trello.
You may considerably reduce the risks associated with maintaining an API by following the rules below, regardless of your niche.
Implement authentication
An API must perform authentication before executing a request; it must authenticate the identity of the person or programme who sent the request.
APIs typically employ a password, multi-factor authentication, and/or an authentication token, which is a string of characters that acts as a user’s unique identification. An API verifies the token given in the request with one stored in its database to authenticate a request using a token. Tokens assist an organization in keeping track of those who are entrusted with its assets.
Implement authorization
An API must be able to allow access to only the authorized resources and methods after confirming the identity of the user initiating the request. For example, a user may be authorized to use the API, but if they aren’t allowed to use the POST method to add data to the application’s database, any request to do so should be refused. As a token, authorization information can also be included in a request.
REST APIs, unlike certain other API types, need each request to the server to be authenticated and authorized, even if numerous requests are made by the same user. This is due to the fact that REST communications are stateless, meaning that the API can understand each request independently of previous queries.
User roles can be used to control authorization, with each role having various permissions. In general, API developers should follow the concept of least privilege, which asserts that users should only have access to the resources and methods required for their role. Predefined roles make it easy to manage and adjust user permissions, lowering the risk of sensitive data being accessed by a bad actor.
Validate all requests
As previously stated, queries from seemingly legitimate sources might occasionally be construed as hacking efforts. As a result, APIs require criteria to identify whether a request is benign, benign but invalid, or destructive, such as an attempt to inject malicious code.
The contents of an API request are only handled when they pass a thorough validation check; otherwise, the request should never make it to the application data layer.
Encrypt all requests and responses.
Any data flow from the user to the API server, or vice versa, must be adequately encrypted to prevent MITM attacks. Without the proper decryption mechanism, any intercepted requests or responses are meaningless to the intruder.
Because REST APIs employ HTTP, the Transport Layer Security (TLS) or its predecessor, the Secure Sockets Layer (SSL) protocol can be used to encrypt data. These protocols are the standard for encrypting web pages and REST API communications, and they provide the S in “HTTPS” (“S” signifying “secure”). Some CMS solutions may give you a free SSL certificate that will encrypt your pages right away. If your platform, such as WordPress, does not include an SSL, you will need to add one using an API or plugin.
TLS/SSL encrypts data only when it is being transmitted. Because it doesn’t encrypt data behind your API, sensitive data should be protected at the database layer as well.
Consider incorporating a web application firewall (WAF) in addition to an SSL to monitor web traffic and detect and prevent DDoS assaults and code injections.
Only include necessary information in responses.
It’s possible that an API answer will mistakenly reveal information that hackers can use, similar to how you would unintentionally reveal a secret when telling a buddy a story. To avoid this, any responses delivered to the end-user should only contain the information necessary to signal the request’s success or failure, the resource requested (if applicable), and any other information directly linked to these resources.
To put it another way, don’t “overshare” data – the response is an opportunity for you to mistakenly expose private information, either through returned resources or verbose status messages.
Throttle API requests and establish quotas.
An API can apply rate-limiting, which limits the amount of calls to the API server at any given time, to prevent brute-force assaults like DDoS.
Quotas and throttling are the two most common methods for rate-limiting API calls. Throttling slows a user’s connection while still allowing them to use your API. Quotas limit the number of requests a user can make in a given period of time.
Both techniques should allow standard API queries while also preventing traffic floods and unexpected request surges in general.
Log API activity
We’ve explored preventative strategies for dealing with API threats up to this point. However, if your system is successfully hacked, you’ll need a mechanism to track out the source of the problem so you can fix it and report it.
This is why recording all API activity is so important: if attackers get past your defenses, you’ll be able to figure out what they did and how they got in. At the very least, you can utilize such an attack to secure your API more, thereby averting future incidents.
Conduct security tests
Don’t wait till a real attack to test how well your defenses work. Allow enough time for security testing, which is deliberately hacking your API to expose flaws. Remember that testing isn’t a one-time event; it should be done on a regular basis, particularly when your API is updated.
API Security Testing
The first step in API security is to ensure that your API is functioning properly. This entails sending standard requests using an API Client while adhering to the guidelines outlined above. Create scenarios that address the following questions:
- Is it possible for just authenticated users to access your endpoints?
- Are users given access to only the endpoints that they need based on their roles?
- Is the information returned in response to each prospective request correct?
- Are requests that aren’t harmful but aren’t genuine rejected?
After you’ve confirmed that your API is functioning normally, you’ll need to test your systems for code injection, MITM, DoS, and stolen password threats in a good testing environment. In your tests, make sure to include the following:
- Is it possible for my authentication to thwart brute-force access attempts?
- How does my API handle large surges in request volume?
- What if a trusted user sends a request that contains a malicious script or file?
- Is it true that all data transmissions are encrypted? Are requests that do not use TLS/SSL (i.e. HTTP rather than HTTPS) prohibited?
- What happens if a request or response is tampered with? How will my API and the user be aware of this?
You can perform the tests listed below.
User Authentication Test
Attackers might compromise authentication tokens or leverage implementation vulnerabilities to assume other users’ identities and obtain access to your API’s endpoints if authentication mechanisms are done incorrectly.
Send API calls without adequate authentication (either no tokens or credentials, or the wrong ones) to see if your API responds with the appropriate error and messaging.
Parameter Tampering Test
To do a parameter tampering test, use different combinations of improper query parameters in your API queries and observe if you get the expected error codes. If not, there are probably some backend validation flaws that need to be fixed in your API.
Injection Test
Try injecting SQL, NoSQL, LDAP, OS, or other instructions into API inputs to check if your API executes them. These commands, like reboot or cat, should be completely safe.
Unhandled HTTP Methods Test
Most APIs include a variety of HTTP methods for retrieving, storing, and deleting data. Unsupported HTTP methods are sometimes granted by default on web servers, making your API insecure.
You should try all of the basic HTTP methods (POST, GET, PUT, PATCH, and DELETE) as well as a few unique ones to test for this issue. TRY using the HEAD verb instead of the GET verb in an API call, or a request with an arbitrary method like FOO. If you obtain a 200 OK response instead of an error code, your API contains a vulnerability.
Fuzz Test
One of the last tasks in your API security auditing process should be fuzz testing. This form of testing necessitates pushing your API to its limits in order to uncover any undiscovered functional or security concerns.
Send a huge number of randomized requests to your API, including SQL queries, system commands, arbitrary numbers, and other non-text characters, and check whether it answers with errors, wrongly processes any of these inputs, or crashes. Overflow and DDoS assaults will be simulated in this type of testing.
6. Allowing Data Filtering, Sorting, Field Selection, and Paging
It is very difficult to manage huge databases. Retrieving only the requested data without exposing the entire database is one of the most difficult aspects of ensuring a secure connection to an API. You need to use a filter to do this so it can return data that responds to the request.
Also it saves a lot of bandwidth on the client side. As your database grows, the need for data filters also becomes more essential. The REST API provides many filtering options:
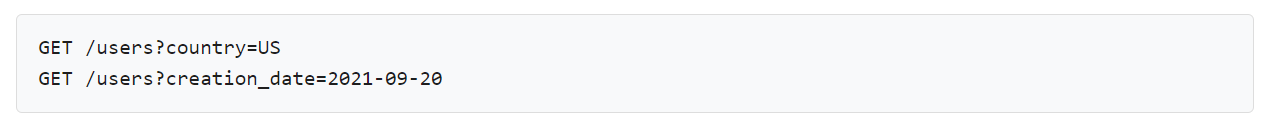
Filtering – This helps to check the results using specific search parameters like country, creation data, etc.
Sorting – This helps you to sort the results in ascending or descending format using your desired parameter like dates, range etc.
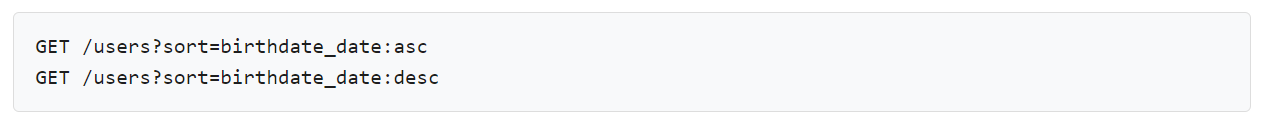
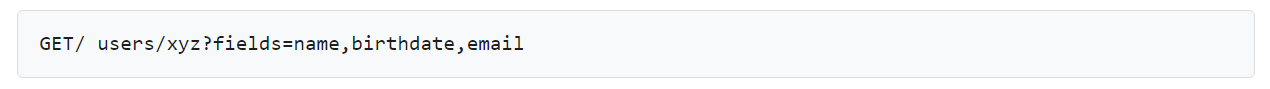
Field Selection – This viable REST API development feature allows developers to request only a portion of data that is accessible to a specific object. Therefore, if the topic you are asking for has many fields like last name, first name, date of birth, phone number, email id and you only need a few, just use field selection to mention the ones you need added to the reaction.
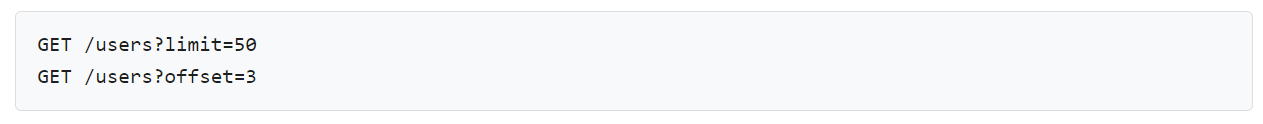
Paging – Use `limit` to check the result in a specific number. Also, it uses “offset” to indicate which part of the result set is presented.
7. Optimizing for Human Readers
As mentioned above, APIs should be easy to understand and use. Besides using JSON, you can use other things to make APIs easy to use and understand:
- Use a clear and simple naming system with no abbreviations.
- Make use of nouns instead of verbs in HTTP methods.
- Have easy to understand and simple descriptions for error handling, as well as standardized error codes.
- Use plural nouns for sets according to accepted standard
8. Keeping Resource Nesting Limited
Resource nesting helps to pair two functions that share a similar or related hierarchy. If you consider the online store as an example, “orders” and “users” are resources in a similar category.
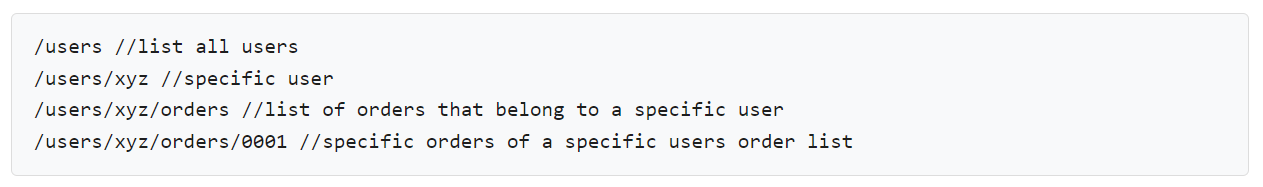
Nesting is an effective practice for pairing meaningful resources. However, many developers abuse it, which reduces its appeal.
In addition, it creates complex dependencies that the basic developer or user cannot understand properly. Thus, making efficient use of nesting your resources is one of the best practices for developing REST APIs.
9. Exploiting Safe Methods
Some safety tactics are HTTP methods that restore the correct representation of resources. The HEAD, GET, OPTIONS and TRACE strategies are considered safe. This implies that they can retrieve data in general without changing the state of the resources on the server. Also, avoid using GET to remove content.
Normally you can run these methods, but when the HTTP specification is violated, problems arise. So use HTTP methods depending on the action you need to take.
10. Name the collections using Plural Nouns
The REST API improvements use plural nouns for collections. It’s not just a long-standing practice. It never makes it difficult for people to get the idea that it is a collection.
Eg.
GET /cars/123
POST /cars
GET /cars
-vs-
GET /car/123
POST /car
GET /car
In the first example, you can see a reference to car number 123 in the entire existing list of “cars”. The plural use of “car” tells us that this is actually a collection of different automobile objects.
In the second example, it is not so obvious that there are other cars in the system.
11. Use Nouns instead of Verbs
In API development, the REST approach can also be called resource-based. So in our application you work with resources and their collections (e.g. a book and a list of all books). Actions on resources are strictly defined by HTTP methods like GET, PUT, POST, PATCH, DELETE (and a few others, less relevant for this example) and only they should be used. Used to change the state of a resource. This brings us to the construction of endpoint URIs. Considering the above, a properly built endpoint should look like this:
Correct way
GET /books/123
DELETE /books/123
POST /books
PUT /books/123
PATCH /books/123
-vs-
Incorrect way
GET /addBook123 (by the way, GET should be only used to READ data and never to change its state in any way)
GET /DeleteBooks/123
POST /DeleteAllBooks
POST /books/123/delete
There are some cases where it is acceptable to use actions like resource manipulation, for example:
PUT /account/123/activation
This is required to create or update the activation attribute on account `123`, rather than just saying that “activation” should be called.
Is it tempting to use something like POST/active_account/123 or PUT/account/123? Active = true but both are incorrect.
12. Create expectations
When working with developers, it’s important to let them know what to expect, when to deliver, and what issues need to be addressed with API functionality.
13. Service messaging
For the purpose of creating new products and services or transforming existing ones, it is paramount to ensure that these services and the APIs that provide access to them are consistent with the business goals and lead to services that deliver value.
14. Case studies
It’s key to again up assumptions with feasible case research that illustrate the upgrades that API adoption brings to the table.
15. SDKs and libraries
The SDK & libraries is a direct path to the API creator’s mind. The various methods, systems, integrations, and services of the API manufacturer are not only present (as they are in the API itself), they are clearly explained and demonstrated – in this way the SDK & libraries provides a set of ‘tools to create’, yes, but also provide a direct, customizable and completely API vendor-managed communication channel to interpret and describe in their own way.
As both a tool for creation and communication, the SDK & libraries must be seen as a critically important two-sided system.
Building a poor SDK & libraries also ensures that any communication between developers and users will be poor, filled with assumptions and extrapolations that may or may not be true. To that end, following some of the methods outlined here will ensure that your SDK & libraries, and the systems that use it, are the best they can be. Also identify the sdk and libraries available in the market instead of reinventing the wheel so your development team can focus on the actual business implementation.
16. Minimize the Number of Network Calls to Reduce Latency
The network performance is extremely important, regardless of how well the REST layer is designed. As a result, network delay can have an indirect impact on the REST server’s responsiveness. The design of the REST layer can often be rushed, resulting in undesired data being transferred back and forth from the REST server to the client.
Compression may be the answer if you want to reduce latency without compromising data. You can use a tool like gzip to compress larger replies before serving them in this scenario. Naturally, this means that your engineers will have to extract responses on the client side.
If latency is a major concern for you, you should avoid using service calls between your components. Instead, reduce the amount of time control transfers to an out-of-band resource by making calls in-process, which is substantially faster.
17. The More the Integrations, the Better
Integrate your APIs with third-party technologies/APIs so that they can collaborate if necessary. It will help you build a more robust platform by allowing your API to do more.
Integrations using open-source libraries or enterprise service buses, such as Apache Camel, MuleSoft, and others, would, for example, make integration easier and minimize time-to-market.
18. The API Should Respond to the Needs of the Consumers
APIs are designed to benefit your customers, not you. Make sure your APIs are adaptable enough to accommodate future changes. It’s also a good idea to make sure your APIs are easy to combine with other technologies/APIs.
Don’t be scared to break compatibility and improve your APIs if you decide to change the structure of your database or add a new type of technology. Your API, for instance, gets data from a database. Allow consumers to use common query clauses like “where” if you provide them the ability to query your database.
19. Make Sure Your APIs Can Scale
Make sure you have a well-thought-out load balancing and scaling strategy in place so your APIs don’t go down when a large number of users try to access them at the same time. It’s a prevalent concern among API developers because they don’t consider how their APIs might be used by other parties.
Let’s imagine your API delivers data to users, and you allow them to query the database. You have no way of knowing how many external sources will simultaneously access your API. It’s a good idea to implement some load balancing technology/methods so that your API doesn’t go down if too many external resources suddenly target it.
20. API Should Not be Monolithic
When it comes to API development, monolithic means “one full block.”
Developing APIs is a bad concept because it makes them appear difficult to understand and use, as well as rigid.
An API that requires users to submit a single request for all conceivable data, for example, is monolithic, making it difficult for users to use. Instead, divide your APIs into smaller request methods that allow customers to simply get only the information they need.
21. Design API for High Performance & Availability
Your APIs should be as fast as workable, which is usually accomplished by limiting the amount of requests. You must also ensure that they are highly available, which may be accomplished by distributing and fault-tolerant them. When building APIs with significant traffic or usage, they are both critical considerations.
Let’s imagine your API isn’t very fast, and a customer uses it thousands of times in a short period of time. This issue should be avoided if your APIs are designed with performance and high availability in mind. It will cause the API to go down, resulting in a poor user experience.
22. APIs Must Use Industry Standards
Industry requirements are the high-quality manner to head while designing APIs. You can use the maximum commonplace requirements available, RESTful APIs, JSON, XML, etc. These are the requirements that maximum builders are acquainted with, so this makes it clean for clients to paint together along with your APIs.
For example- Let’s say you layout every other popular API utilization that won’t be as famous or broadly used. There might be a loss of documentation due to the fact fewer humans realize the way to use them, and clients may get annoyed due to the fact they don’t realize the way to paint with the APIs. Using enterprise requirements, documentation and different substances might be broadly available, making it clean for clients to apply them.
23. Keep Service Boundaries Well Defined
Service limits define the limits to which a service can be used or accessed.
It makes sure that your APIs are designed to be reusable and modular. A good analogy is that if you were building a car, you wouldn’t build a big car with all the same parts, because that would make it less efficient. Instead, you’ll design smaller vehicles, all of which are different but can be used together.
Consumers need to know what the limitations of the service are in order to work properly with them. If they are not identified as two different services, then both must run concurrently in order to function correctly. For example, let’s say you have two APIs, one for driving and the other for giving directions.
24. SEO is Essential Always
For any website or API to rank well, search engine optimization (SEO) is essential. It’s not only about having a strong product; SEO is crucial for getting the word out and letting people know about your APIs. To make it easier to rank in search engines, make sure your documentation is SEO optimized.
For example, if you make too many changes to the design of your documents without improving your SEO, consumers will have a harder time finding them and will be less inclined to use them. Keep your SEO optimized to improve your ranking and spread the word about the APIs. Please note that this is needed only for public or open sources API’s.
25. API Design Should be User-friendly
The design of an API should be simple and intuitive. Consumers may become frustrated and discontinue utilizing APIs if they can’t figure out how they function. This lowers API adoption rates, making it more difficult to market them. Keeping your documentation and actual design user-friendly enhances the likelihood that people will use them.
If your APIs aren’t intuitive, for example, customers will have to spend more time learning how they function rather than simply checking them out to see if they meet their needs. As a result, customers must assess whether an API will be available in a reasonable amount of time in order to avoid wasting their time.
26. Swagger
Swagger is a well-known and commonly used tool for documenting REST APIs. It provides a method for analyzing the use of a specific API, allowing developers to understand the fundamental Semantic behavior. To be more specific, it is an analytical method of adding documentation via annotations, which results in a JSON file that specifies APIs and their use.
27. Idempotence (Misusing Safe methods)
Some secure methods are HTTP methods that return an exact representation of the resource. The GET, TRACE, OPTIONS and HEAD methods are considered safe. By safe way we mean that they are ideally expected to retrieve data without changing the state of resources on the server.
Also, avoid using GET to delete stuff, like GET /users/123/delete.
In general, there is nothing to make it unenforceable, but the problem arises because the HTTP specification is violated in this case. Therefore, use HTTP methods depending on the action you need to take.
28. Layered System
A client cannot ordinarily tell whether it is connected directly to the end server or an intermediary along the way. Intermediary servers may improve system scalability by enabling load-balancing and by providing shared caches. Layers may also enforce security policies.
29. Use kebab-case for URLs
The kebab case naming convention gets around this limitation by using a dash instead of a space between words.
The phrase is derived from the picture of a skewer in a kebab. On a shish kebab, the skewer pierces many pieces of food together. The dash in code signifies the skewer, which holds numerous words together to explain the meaning of a resource, similar to a shish kebab.
Kebab case examples
Here are three examples of the kebab case naming convention:
- descriptive-variable-name
- INTERESTING-TEXT-FILE
- naming-conventions-webpage
30. Use camelCase for Parameters
Pascal case or higher camel case refers to when the first letter of a camel-cased variable is uppercase. Lower camel case is the name given to it when it isn’t.
 30. Use camelCase for JSON property
30. Use camelCase for JSON property
UpperCamelCase is the name of the type and protocol. For object/struct property names, this standard employs lower camel case (camelCase). In this case, we can encode and decode JSON objects without any alterations right out of the box.
31. Don’t Use table_name for the Resource Name
The following are the guidelines for naming database objects (such as tables, columns, views, and database procedures): Only alphanumeric characters are allowed in names, and they must begin with an alphabetic character or an underscore ( ). The first character in a database name must be an alphabetic character, and it cannot be an underscore.
33. Accept limit and offset Parameters
To paginate across items in a collection, APIs that support offset-based paging use the offset and limit query parameters. When the list of items has a fixed and predetermined length, offset-based pagination is frequently used.
34. Take fields Query Parameter
Using the fields query parameter, you can limit the fields that appear in a response to only the ones you’ve asked for. Filtering the fields returned in the answer can help you save bandwidth and speed up your response time.
35. Don’t Pass Authentication Tokens in URL
Authentication tokens should not be included in page URLs: Authentication tokens SHOULD NOT be included in page URLs (for example as query string parameters). Instead, bearer tokens SHOULD be sent in HTTP message headers or message bodies that are protected by encryption.
36. Validate the Content-Type
The client will define the Content-Type (e.g. application/xml or application/json) of the incoming data when POSTing or PUTting new data. The server should never take the Content-Type header at face value; it should always verify that the Content-Type header and the content are of the same type.
37. Use throttling and rate-limiting
Throttling involves setting a temporary state that allows the API to evaluate every request and is often used as an anti-spam measure or to prevent abuse or denial-of-service attacks. There are two primary considerations when implementing the throttling feature: how much data should be allowed per user, and when should the limit be enforced?
38. Scan for API Vulnerabilities
To maintain the continued security of API services, it is essential to enable automated scanning, identifying vulnerabilities, and mitigating them at all stages of the software lifecycle. Automated scanning tools automatically detect vulnerabilities by comparing application configurations with a database of known vulnerabilities.
There is a network component and an important program in the cross-link of attackers is serious enough, but with API, the situation is even more precarious because of the lack of standards related to their creativity. Many organizations may not know how many APIs they use, the tasks they perform or how much authorization is. After that, there are questions whether these APIs contain vulnerabilities.
API testing tools and platforms have been developed by industry and private entities to help address those concerns. Some testing tools are built to do a single task, such as determining why specific Docker APIs are configured incorrectly.
Others take a more comprehensive approach to a network, looking for APIs and then explaining what they do and why they can be susceptible or over-permissioned.
There are several well-known commercial API testing platforms available, as well as a significant number of open-source solutions that are free or low-cost. Commercial products typically come with more support options and can be implemented remotely via the cloud or as a service.
Some open-source programmes may be just as good as commercial products and have the support of the users who created them. Which one you choose is determined by your requirements, your IT team’s security competence, and your budget.
APIsec
The APIsec platform acts as a penetration tool targeting APIs. While many tools can search for vulnerabilities common to typical attacks like script insertion, APIsec checks every aspect of targeted APIs to ensure that everything from the core network to endpoints that access it are protected from API code vulnerabilities.
AppKnox
AppKnox provides a lot of support to people that buy and use their platform. AppKnox is a suitable alternative for organizations who don’t have huge security teams dedicated to their APIs because of its easy-to-use interface. AppKnox begins by scanning for APIs in the production environment, on endpoints, or anywhere else they might be deployed. Users can then choose which APIs they want to submit for further testing once they’ve found them.
Data Theorem API Secure
The Data Theorem API Security Platform is designed to integrate with any continuous integration and continuous delivery/deployment (CI/CD) environment to provide continuous API security at every stage of development and across the entire environment of production. Its scanning engine continuously scans the network for new APIs and can quickly identify those that are not allowed or part of an organization’s shadow IT.
Postman
While Postman is clearly an API testing tool, it is most known for being a comprehensive and collaborative platform for developing safe APIs. For good reason, millions of developers working in Windows, Linux, and iOS environments rely on it.
Postman provides a complete set of API tools for developers to utilize when creating new APIs, as well as a secure repository for code that organizations can accumulate over time. Using the secure repository from the start can ensure that future APIs adhere to strict security and organizational criteria.
Use an API gateway
An API gateway decouples the client interface from the collection of backend APIs, delivering a centralized resource for consistent availability and scalability of API services. Apart from managing various API services, the API management platform also handles standard functions, including telemetry, rate limiting, and user authentication, to maintain security between internal services. The gateway acts as a reverse proxy gatekeeper that accepts all API calls, coordinates the resources required to service them, and returns the appropriate results post-authentication.
Developing enterprise-grade APIs is not an overnight task and adopting the best practices can help you bring out the best in the APIs you develop. Modern APIs have features that have made it extremely valuable and useful. They follow standards, like HTTP and REST, that are easily accessible, engineer-friendly, and understood by all, and treated more like products than codes. It also has its own lifecycle, just like software development – designing, testing, building, managing, and executing.
To know more about how to develop robust APIs that can withstand unforeseen circumstances, do drop us a line on connect@walkingtree.tech!












