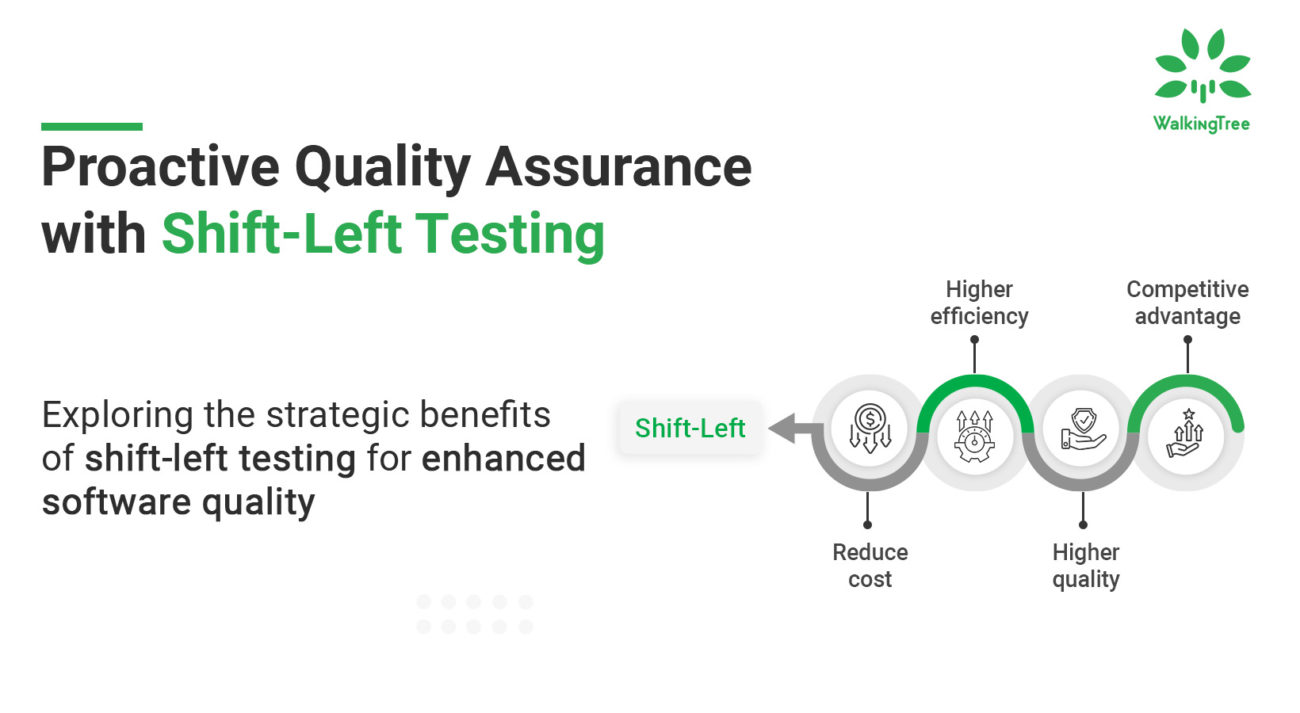
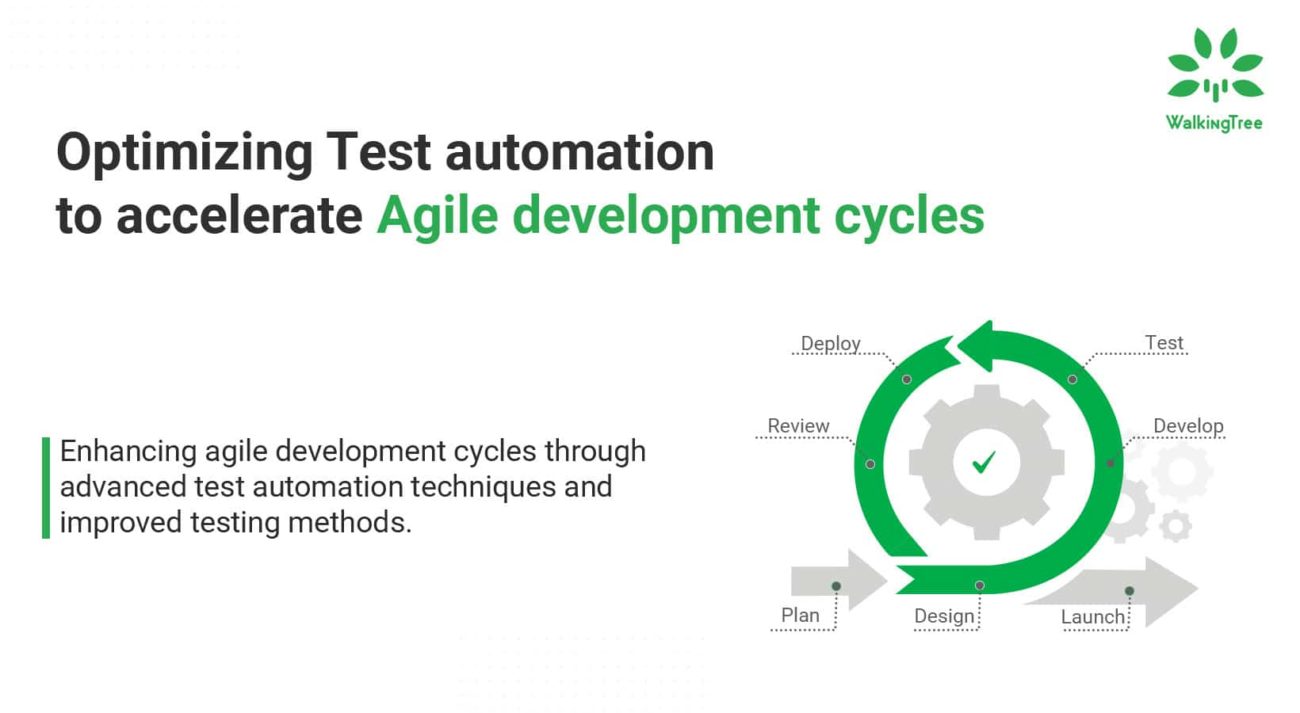
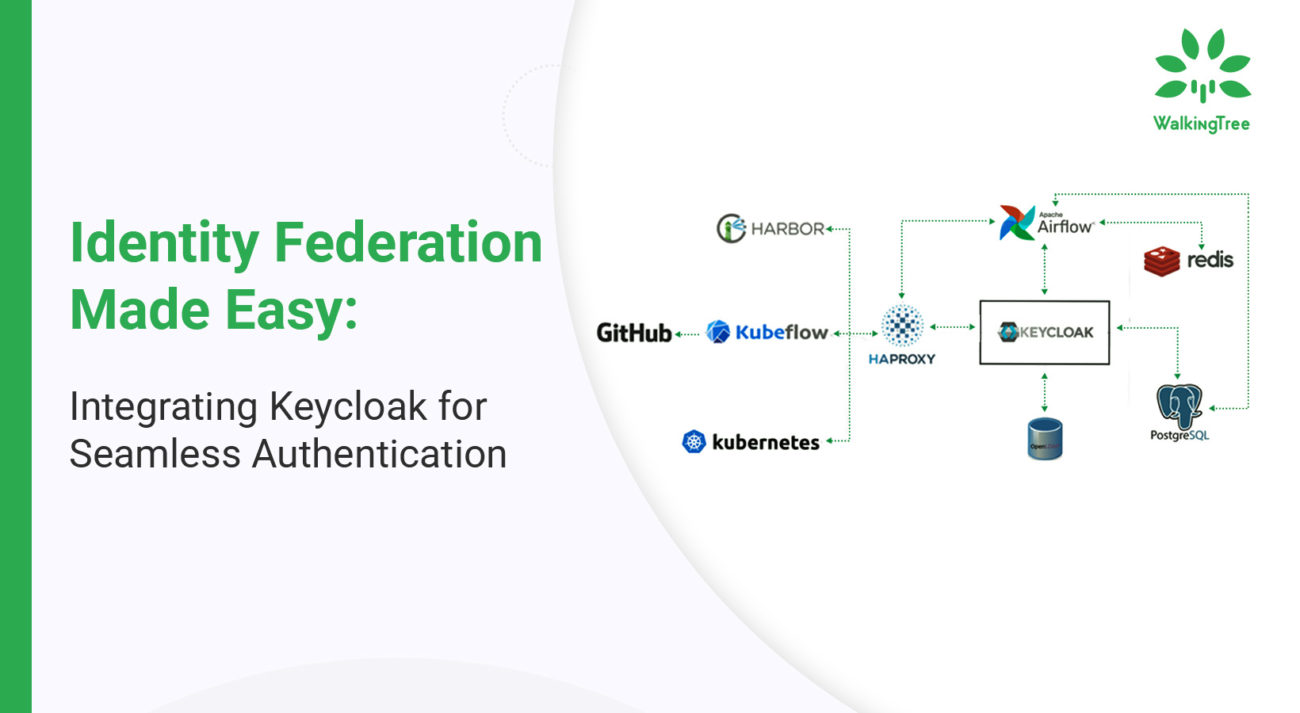
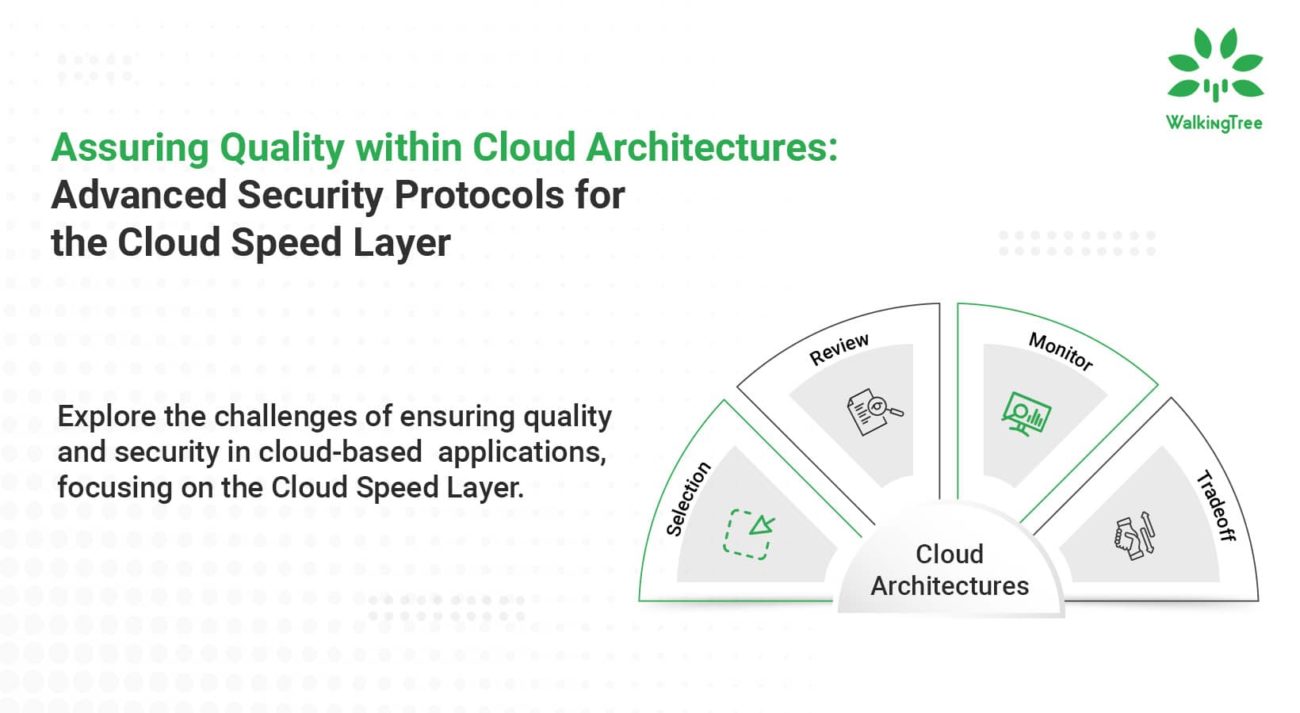
DevOps Benefits from Managed Detection and Response (MDR) Solutions


MDR (Controlled Detection and Response) is a controlled cybersecurity service that gives organizations continuous active monitoring and intelligence-based threat detection, allowing them to act and remediate threats quickly.
Managed Detection and Response (MDR) is an automated managed security service that provides information on threats, threat hunting, safety tracking, analysis of incidents, and response to incidents. These services are a series of cybersecurity solutions focused on network, host, and endpoints that a third-party provider manages for a client organization. Usually, the provider installs technology on the premises of the client organization and offers applications for additional external and automated services. Usually, the provider installs technology on the premises of the client organization and offers applications for additional external and automated services.
How does it work?
After scanning for threats and responding to them once identified, MDRs enhance cybersecurity. They also enable users to communicate with the security experts of the provider, who can help improve the IT department of the client company’s security skills. This makes them perfect for organizations that do not have a designated in-house threat detection unit.
Due to expanding digital transformation culture and the rising skills gap in cybersecurity, Managed detection and response services are growing in popularity. In 2018, Gartner predicted that 15% of mid-to large-sized businesses would use MDR services in 2020, compared to the 1% that used them in 2018.

Problems solved by MDR
An active role is played by MDR services in strengthening a business’s information security policy. Threat identification, incident response, continuous IT asset tracking, and analysis are done by them. These tasks are approached by MDR services in a manner that mitigates common problems that modern IT departments normally face, such as:
Volume of high alerts — MDRs help enterprises handle the sheer volume of cybersecurity alerts that need to be individually checked. Smaller security teams may be frustrated by too many warnings and cause them to neglect other duties.
Analysis of threats—Many security alerts do not present themselves as a danger immediately and in such cases there is a need to carefully analyze to evaluate their status. To assist with this, interpreting incidents and making suggestions for change, MDR services include advanced analytics tools and access to security experts.
Shortage of skills — The CIA recently reported that there will be a 1.8 million security workforce deficit by 2022. Also, it was reported that four out of every five surveyed security professionals report feeling stressed out and in a persistent overload condition. By allowing access to their team of experts, who normally work 24/7 to track a network and are available for consultation, MDR services may minimize this.
Endpoint Detection and Response (EDR) — Businesses that lack the resources, time, or expertise to train EDR tools for employees. MDR services come with EDR tools and incorporate them into processes of identification, review, and response, removing the need for extensive security of in-house endpoints.
Organizations trade some control for more convenience and more flexible costs, as with many X-as-a-service (XaaS) models that outsource modern IT procedures. In contrast to older managed security products and depending on the planned usage of the client for the services, MDR services have several downsides. Their biggest advantage, however, is that they are ideally suited to the existing and emerging challenges facing IT businesses today.
How Managed Detection and Response (MDR) Solutions Benefit DevOps

DevOps has transformed the development of apps. However, modern methodologies can introduce security flaws through your sensitive applications. Fresh, highly sophisticated attacks are infecting the code before it even gets into production, in addition to simple security lapses in the rapid-cycling DevOps phase. As a consequence, if it is ever detected, malware will potentially infiltrate millions of devices before being detected.
Though (MDR) is a relative newcomer in the field of cybersecurity, is beginning to have a significant effect on businesses looking to protect their operations better. Companies adopting new methodologies like DevOps are also taking measures to protect their software from security breaches. MDR provides companies with clear advantages, but when MDR is combined with DevOps, there is a tremendous opportunity. To incorporate cybersecurity into their production and deployment pipelines, several organizations are shifting to DevSecOps methodologies and MDR may help.
DevSecOps is misunderstood in most cases as people think of DevSecOps as an extension of a department of quality assurance, which means that cybersecurity is essentially an afterthought and not part of the development cycle. There is an interesting point that as more organizations attempt to implement DevSecOps, knowledge, along with the action, is lacking and MDR has the potential to supplement knowledge and insight into the security aspect of the code being generated.
Leaving cybersecurity to the network or operations teams, organizations assume that endpoint or network security tools alone contain threats. Many threats in the wild, however, can exploit older code, or target unpatched apps. By keeping developers updated about emerging threats and vulnerabilities, as well as integrating tools for continuous cybersecurity into the development and deployment pipelines, MDR will allow DevOps teams to get ahead of the latest threats. Providing access to experts who can take steps to prevent an attack is one of the key principles of MDR. According to the Business Strategy Community, which estimates that 51 per cent of survey respondents face a problematic shortage of cybersecurity expertise, this is a significant factor.
MDR becomes a tool for developers to make more secure code as well as securing the DevOps environment. “Before threats impact DevOps, it is important to find advanced threats, ones that may have bypassed existing security controls. However, individuals need to be made aware of those threats so that they are not mistakenly included in the development pipeline.
Impact of Covid19 on Cybersecurity

Due to the Covid-19 pandemic, the digital transformation of businesses is accelerating, and cybersecurity is now a major concern. Stay at home restrictions imposed by the Covid-19 has encouraged employees to work from home by many enterprises where technology became more important in work life and personal as well. The pandemic inflicted unprecedented circumstances on businesses across the world and for many enterprises, the change in the paradigm has led to quickly adopt new methodologies that enable them to seamlessly deliver services in a smart way to ensure business continuity. This is where DevOps has become a survival imperative for many businesses and nevertheless, strong adoption of DevOps can help organizations quickly deliver value to end-users. DevOps is designed for remote workspaces, by default.
This involves an automated approach for software development that does not discriminate whether the team operates remotely or on-premise and due to its autonomous and distributed existence, during the ongoing crisis, DevOps may offer all the necessary boost to business deliveries. And for enterprises with DevOps adoption to make continuous deliveries, many endpoints have to be created to make more services available to end-users. However, for hackers, each new endpoint provides a possible entry point. MDR is an excellent method of securing endpoints, between continuous surveillance and threat hunting. The ability to secure entry points quickly is why companies are being successful with Managed Detection and Response(MDR).
AI-Driven Managed Detection and Response

MDR services usually use omnichannel analytics to process vast quantities of global and organizational data from different sources, such as networks, devices, endpoints, user access, etc. Artificial intelligence is used both inside and outside the framework to detect potential threats, vulnerabilities, and possible breaches, whereas human cybersecurity experts act on observations to provide holistic protection.
Using such technologies like AI, one need not wait for an alert, security teams can simply hunt them. Using data science and machine learning algorithms, any suspicious and anomalous activities can be detected. Further, a specialized team analyzes these activities and thereby examines the data to identify threats that might have evaded other security controls and helps security teams to easily avoid attacks.
Both within and outside the system, artificial intelligence is used to identify potential threats, vulnerabilities, and possible breaches while human cybersecurity experts act upon to deliver holistic defence. vulnerabilities and potential threats relevant to a specific IT system can be analyzed by leveraging AI and much before an attack is actually launched it can anticipate known and unknown threats to hunting them down. With real-time rules to detect attacks and compliance violations Security logs and events are additionally evaluated The only realistic solution in an increasingly volatile and threat-prone business environment is to make AI-driven MDR an integral part of cybersecurity systems as the world becomes more interconnected and digitally-led.
Choosing an MDR Provider
Choosing a provider that fits into a DevOps and enterprise strategy can be overwhelming with so many players in the MDR space. Today, providers number in the thousands, and while many say they have “complete” deals, along with conventional network operations issues, they do not consider the needs of DevSecOps. When choosing an MDR platform, there are some significant considerations. The visibility of the attack surface, for example, is a vital concern. If an MDR provider does not have insight across all possible attack surfaces, there will always be breaches and compromises. Adopters should also be keenly aware of the containment of false positives, as well as the extent of warning behaviour. Alert fatigue and obscure efficacy may be introduced by many cybersecurity solutions. Automation should be a key component of any MDR solution, as it can help without human interaction to categorize threats, initiate responses and identify the latest threat trends.
Conclusion
Today’s global cybersecurity world is more difficult than it has ever been before. The growing use of smart devices and the Internet of Things (IoT) has led to a complete dissolution of the perimeters of the previously protected network. In this blog, we have discussed how MDR services can extend cybersecurity. However, choosing the right service that your organization needs is the right step that you take towards when opting for MDR service. Ultimately, in the ongoing war against cybercriminals, MDR is about individuals, systems, and technology, and the IT industry should start practising to put these elements together to ensure success.