Blogs
Introduction to Keycloak and the Need for Containerization


To understand Keycloak, let’s first get a quick overview of identity management.
Identity Access Management
Identity Access Management or IAM as its name suggests is used to authenticate user identities and their privileges. You use this framework to check whether users have access to the resources that they need access to. Moreover, you can use it to identify users who have access to specific information and modify it according to your needs.
IAM is now a requirement for all modern software projects. Earlier, developers would need to create their own application specific user management infrastructures, but now with frameworks like Keycloak, this has become an easy task.
There are about three things that run in common with all IAM infrastructures:
- They can create, manage, and delete identities without regard to access or entitlements.
- They come with a function that allows their users to log on to use their services.
- They rely on federated identity to authenticate users.
Now that we’ve understood the basics of IAM, we can move on to understanding Keycloak.
What is Keycloak?
Keycloak is an open-source IAM solution that helps its users secure applications without having to write complex code. This helps save time spent on development.
Keycloak comes with many features. Here’s a list of a few of them:
- User Federation (Active Directory, LDAP)
- Single sign-on and single sign-out
- Standard protocols (OAuth2.0, OpenID Connect)
- Password policies
- Social login
Why Use Keycloak?
Reliable
One reason Keycloak is so reliable is that it follows the standard security protocols for its single sign-on solution. In fact, Red Hat trusts Keycloak (upstream product) for their Red Hat SSO (downstream product), which handles all of Red Hat’s authentication and authorization system.
Keycloak is reliable also due to its licensing – which comes under Apache License Version 2.0. Although you don’t have to take our word for it, Keycloak has an active open source community further proving its reliability.
Supports Standard Protocols
Keycloak offers support for these standard protocols:
- OAuth 2.0
- OpenID Connect
- SAML 2.0
What this means is that any tool or application that can integrate with these protocols can also be plugged into with Keycloak.
What this means is that Keycloak can be plugged into any tool or application that can integrate with these protocols.
Security
Keycloak takes care of authentication, relieving applications from working to safely store passwords or use different authentication mechanisms. This increases the level of security since the applications will not have direct access to user credentials. Instead, applications are given security tokens that give them access to specific information.
Easy to Get Started
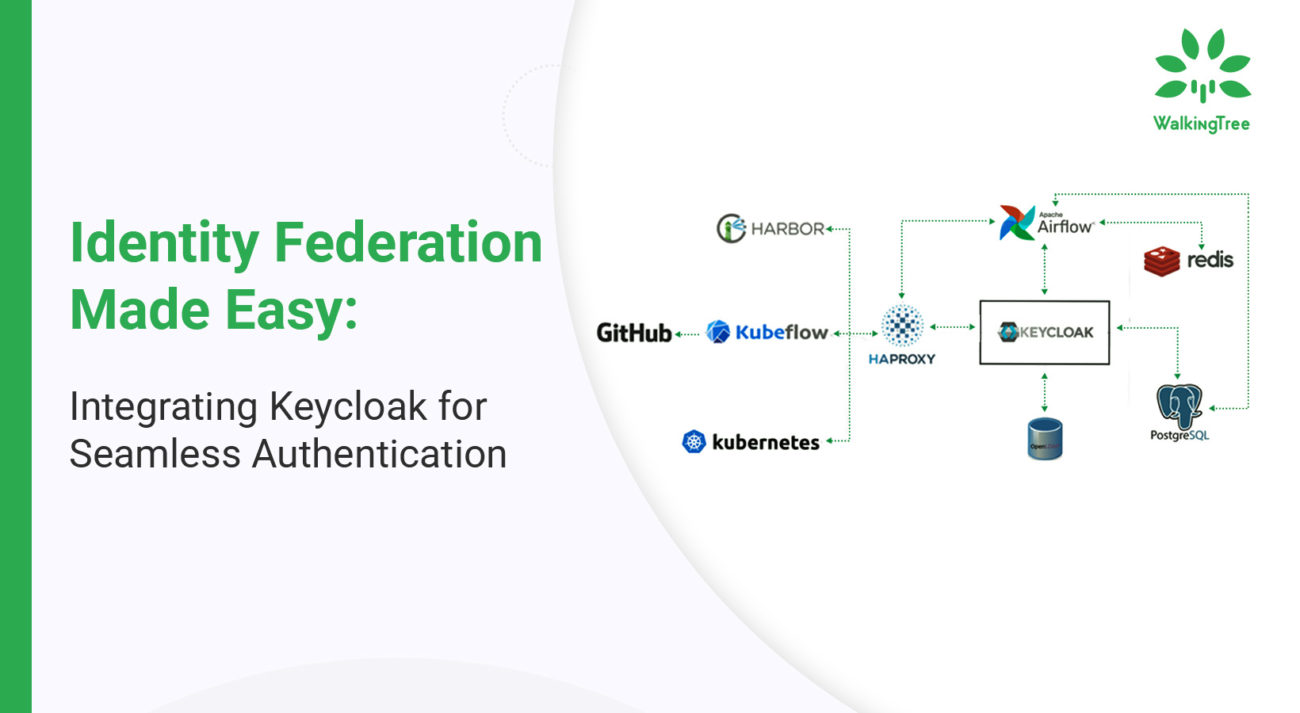
Since Keycloak comes with its own user database, it makes it easy to get started with. Additionally, it is also easy to integrate it with your existing identity infrastructure. This is possible through its identity brokering capabilities that allow you to plug in your existing user database from other enterprise identity providers.
You can integrate Keycloak with directories like Active Directory or LDAP servers as well.
Customizable and Extendable
Keycloak is highly customizable and extendable. It has a large number of extension points that allow you to deploy custom code. You can use this feature to modify certain behaviors or even add new capabilities. These include unique authentication mechanisms, custom manipulation tokens, custom user stories, and even custom login protocols.
How it Works
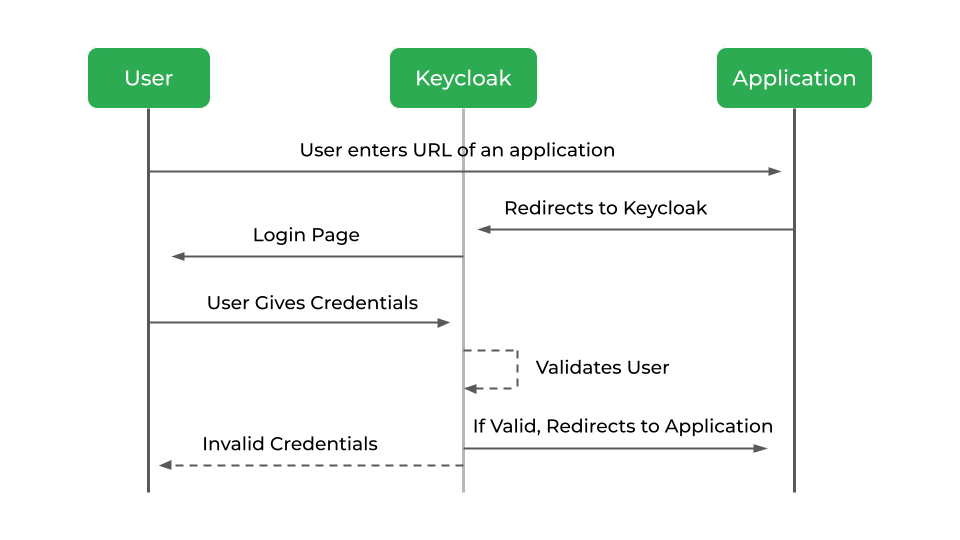
Once a user secures his system with Keycloak, here’s how it works:
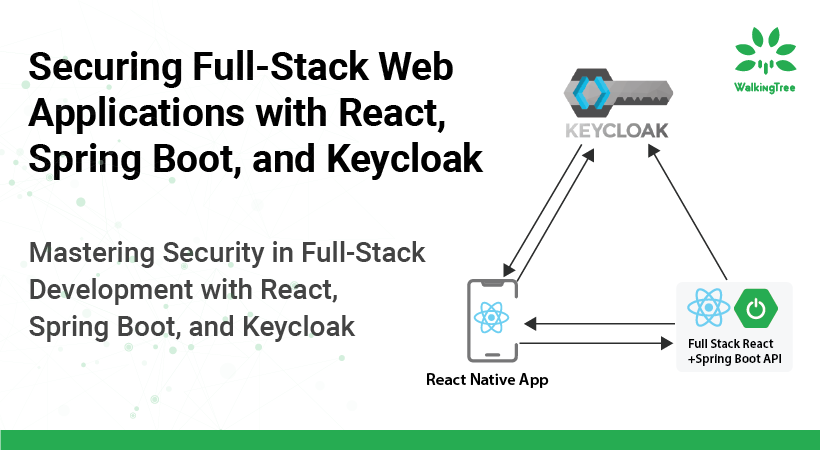
When the user tries to navigate to a protected application, he is first redirected to the Keycloak authentication page. Once he enters his login credentials, Keycloak will redirect the user to the application with a code.
The application exchanges this authorization code with an ID and access token. The application can then use this ID or access token to authenticate the identity of the user.
Getting Started With Keycloak
To start using Keycloak, you’ll first need to set it up. Here are a few steps:
- Install and boot your Keycloak server by downloading the server zip file, unzipping it, and booting it using standalone.bat in windows and standalone.sh, in Linux
- Once the server boots, you can open the server in your browser using http://localhost:8080/auth and see the welcome page which shows that the server is running.
- First create the admin account, using which you can log in to the master realm’s administration console, from which you can create other realms and users and also register your applications to be secured by Keycloak.
You can find all the steps on our blog – A Detailed Guide to Securing React Applications with Keycloak.
While modern applications have brought forth amazing solutions, their complexity can bring many challenges. Working to deploy new features, or updating code can get tricky as the size and complexity of applications increase.
A great solution for these challenges is containerization.
The Benefits of Containerization
Portable
You can use containers to bundle all dependencies. This allows you to take your application anywhere without the need to rebuild it for each new environment.
Additionally, containers provide abstraction which ensures that regardless of where you deploy your application – the cloud, run it on a VM, or wherever – it will work the way it’s supposed to. (As long as the OS on which you’re running your container supports your containerization tools.)
Agile
Often, organizations are seen using containerization tools to streamline their DevOps workflows. They can do this because containerization makes orchestration possible.
What this means is that when the need arises, you can instantly develop containers to handle the need. Once the need is met, you can shut the container down and reuse it when you need it next.
Secure
Containers are generally isolated from each other. This isolation provides extra security because you can be sure that your applications are contained in their own environment.
The reason this is beneficial is that even if the security of one container is compromised, the other containers on the same host are safe. Furthermore, containers are even isolated from the host OS only interacting with it minimally.
Keycloak, Containers, and You
While the benefits of using Keycloak and Containers are clear, having both work in tandem brings in more benefits.
If you have any questions that you would like to ask, please reach out to us at connect@walkingtree.tech.