Blogs
Advancing Business Workflow with Electronic User Access Management (EUAM)


Did you know that 92 percent of small-to-medium-sized businesses deal with identity challenges in their environments?
Businesses need to meet the access requirements of a diverse landscape of users across numerous applications while ensuring adequate security. However, even slight mismanagement of the user credentials or access permissions might lead to unprecedented security threats.
Whether it’s email addresses or passwords, user information can be difficult to track without a proper control system. The access given to them plays a critical role in protecting your organization’s resources. And with the enormous amount of data to be processed, stored, and transmitted, scenarios that require modifications to access permissions arise daily.
To meet these demands, your business requires a reliable and flexible access control solution. This is where Identity/User Access Management (IAM/UAM) comes into play.
What does a business-oriented IAM need to provide for improving the workflows?
Over the years, business-oriented approval workflows have modernized rapidly; particularly in the field of authorization allocations, withdrawals, and amendments. This is largely responsible for ensuring that your employees have the right access at the right time.
We tend to think of workflows and cybersecurity as a binary, i.e., your enterprise must select one or the other. The choice often leads to choosing one path at the expense of the other. However, IAM improves the workflow, cutting down the option of choosing between the two. With the help of a reliable IAM solution, you can easily manage both your organization’s cybersecurity and authentication in the workflow.
“About 45% of data breaches in the last year involved hacking and over 80% of those involved the use of lost or stolen credentials.”
Today, IAM systems form the backbone of the compliance policy, offering reliability, transparency, traceability, flexibility, and performance. Thus, forming an intrinsic part of modern IT concepts. IAM solutions are equipped with several features that allow users and admins to simplify the procedures while working for an enterprise. These include:
- Automatic provisioning of accounts
- Self-service management
- Single Sign-On (SSO)
- Role-based access control/access governance
- Audit and compliance
#1. Onboarding and Offboarding Data
If you have ample users or employees but not a proper time management strategy, it simply leads to the waste of resources. So, what can you do?
For instance, the initial creation of a user. This can either occur manually within the identity management system or could be triggered from an HR system. The process involves provisioning the user within the core systems of the company and adding them to the proper groups. Access rules are created and account access is provisioned. This makes the overall automation of account provisioning easier for your IT teams.
Additionally, it also helps with the offboarding process by coordinating the employees with the permissions they should be permitted. Thus, allowing faster permission adjustments and better processes.
#2. Handle temporary permissions with ease
A conditional role binding strategy can be used through IAM for granting time-bounded access to the users. This ensures that a user can no longer access the resource after the specified date and time. For instance, an employee while being off-site may want to read a certain file. In such cases, they have to request the access code from the administrator. The administrator, in return, generates an access code and mails it to them. The user must then apply this code to verify the authenticity and get temporary access permissions.
While not removing temporary privileges can become an immediate security threat, not granting them on time can hinder the progress. The UAM should focus on providing the workflow by automating the temporary permissions to be granted and revoked.
#3. Focus on Multi-Factor Authentication
Business leaders and IT departments constantly work to protect access to intellectual property. With an ever-increasing list of authentication features – including biometrics, AI, and behavior analytics – EUAM is well-suited to the rigors of the new security landscape.
It should emphasize the importance of multi-factor authentication. The process often works in the background evaluating factors like time of access and geographic location to ensure that the right person logs in. When tied with the device or biometric authentication, it can protect the resources from any kind of security breach.
#4. Creating ad-hoc access management workflows
With a business-oriented workflow, these exception processes must be controlled by smart delegation, escalation, and ad-hoc change options during the run-time. The workflow of your organization should not be interrupted by any irregularities or error sources. It should continue to process in a solution-oriented manner and should also be able to track all activities completely.
With standardized access management workflows, you can easily gain insight and control of your business processes relating to authorization. The responsible people (managers and administrators) can view all activities in the process overview and intervene if necessary. Hence, the processes can be monitored and controlled more effectively, reducing the throughput times.
#5. Managing access governance
Access governance transfers the decision-making power and responsibilities to the required departments, to secure important business resources. Your enterprise must start with simple, business-oriented approaches to implement efficient and revision-proof requirement workflows.
Through access governance, your administrators can easily manage the permissions given to the users and perform a regular check on existing rights.
The basic components of an effective EUAM solution
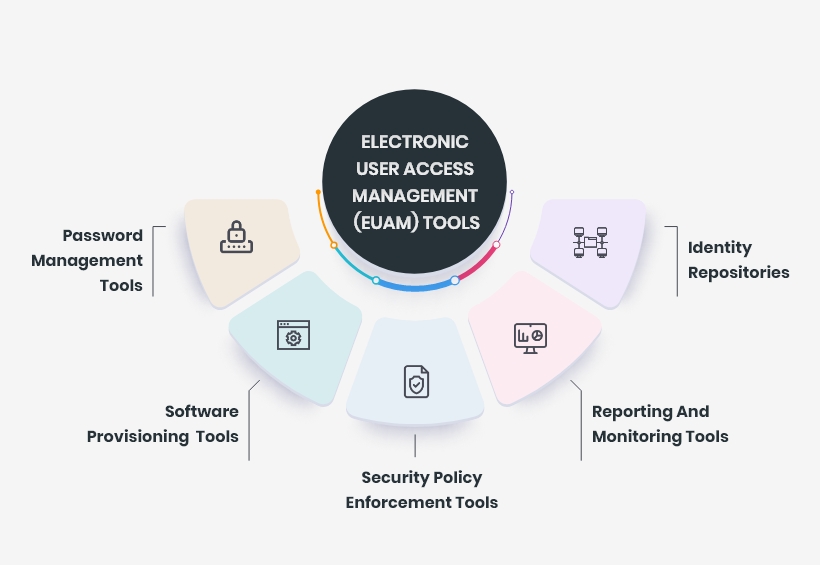
A EUAM framework enables your IT team to control user access to critical information and resources within your organization. An effective EUAM product offers role-based access control, which allows the system administrators to regulate permissions to systems or networks based on the roles of individual users within the enterprise.
In this context, user access is the ability of an individual to perform a specific task such as view, create, or modify a file (based on their roles). A well-setup EUAM product must capture and record user login information, orchestrate the assignment and removal of access privileges, and manage the enterprise database of user identities. It should provide a centralized directory service with visibility and oversight into all aspects of the company user base.
In the cloud, EUAM can be handled by identity as a service or authentication as a service. However, in both cases, a third-party service provider is responsible for authenticating, registering, and managing user’s data.
Common business drivers for adopting IAM successfully
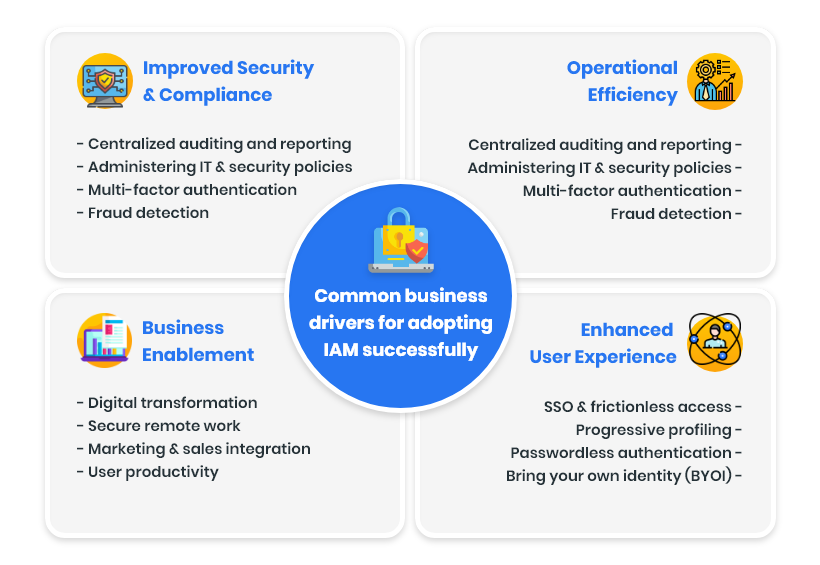
IAM adoption is strongly related to the degree of industry regulation. The business drivers for implementing IAM might vary across organizations and categories. However, the key drivers are the same across the industries for both local and global scales. Here we have the four most common business drivers that influence identity access management:
1. Improved Security & Compliance
- Centralized auditing and reporting
- Administering IT & security policies
- Multi-factor authentication
- Fraud detection
2. Operational Efficiency
- Data aggregation & integration
- Fewer support & operations staff
- Automation of routine tasks
- Integrated life cycle management
3. Business Enablement
- Digital transformation
- Secure remote work
- Marketing & sales integration
- User productivity
4. Enhanced User Experience
- SSO & frictionless access
- Progressive profiling
- Passwordless authentication
- Bring your own identity (BYOI)
Enhancing business yield by incorporating EUAM for your enterprise
Besides ensuring regulatory compliance, enabling cost savings, and simplifying the customer experience, EUAM can be beneficial in several other ways:
- Improves business productivity by automating the entry of new personnel and facilitating access (for both new and existing users) to all the components of the system.
- Optimizing user experience through Single Sign-On (SSO). Thus, allowing customers and partners to access different internal and external applications with the same access method.
- Secures your brand at all levels from security breaches by making sure that regardless of whether a connection is made from multiple identity providers, your data remains safe.
- Granting access privileges based on your organization’s policies. All individuals and services are properly authenticated, authorized, and audited.
- Enhanced user experience as IT admins can create a unique digital identity for every user. This eliminates the burden on users to manage dozens of accounts for various corporate actions or applications.
Emphasizing the challenges faced while implementing EUAM
Despite the significant growth of user access management tools in the industry, they come with many risks and challenges. One issue is – how user’s “birthright access” policies evolve (the access rights that are given to new users when they begin working at a company). The options for how new contractors, employees, customers, and partners are granted this access touch on numerous different departments. However, delegating this to the right people and managers becomes an issue.
This level of automation becomes imperative if we consider automating on and offboarding of users, user self-service, and continuous proof of compliance. The IAM systems should be able to detect access rights changes automatically, but they often don’t.
While zero trust networks are moderating the leading sectors now, the issue arises when these trust relationships are required to be continuously monitored as new applications are added to a corporation’s infrastructure. Besides this, the following configuration oversights should be avoided- incomplete provisioning, poor process automation, and insufficient reviews.
Hunger to evolve and boost security using IAM solutions
IAM is a central practice that protects sensitive business data and systems. It provides confidence that only authorized and authenticated users and admins can interact with the system to perform their job roles.
The IAM starts with an evaluation of your enterprise’s needs that include access requirements, the definition of roles, the creation of a policy, and other valuable features. The more seamlessly a user access management tool fits your organization, the more likely you are to close the security gaps and improve the operations.
User access management has evolved over the years. WalkingTree’s modern, feature-rich, and malleable EUAM solution can adapt to every organization’s size, structure, and hybrid environment. Thus, protecting your company resources and providing the right access at the right time to all the users. It provides IT and security teams with full visibility into how data is being accessed, used, and moved around the organization.