
Blogs
Designing Role-Aware MFA Policies in Enterprise Keycloak Deployments


As enterprise systems grow, authentication stops being a simple gate at the front door. The same identity platform often supports a wide range of users: employees accessing internal tools, administrators managing infrastructure, support teams handling user issues, and operations staff maintaining production systems.
While most users perform routine actions, a much smaller group holds access that can change configurations, manage identities, approve transactions, or affect live environments. The security expectations for these roles are naturally different. Treating them the same may look consistent on paper, but it rarely reflects how risk actually manifests in enterprise systems.
Multi-Factor Authentication plays a critical role in reducing the risk associated with compromised credentials. Breach investigations across industries consistently show that stolen or misused credentials remain one of the most common ways attackers gain an initial foothold. Passwords alone are no longer sufficient protection for systems that support sensitive data or operational control.
MFA raises the bar by requiring additional proof of identity, making stolen credentials far less useful on their own.The real challenge is not deciding whether MFA should be used. Most organizations have already crossed that line. The harder problem is deciding how MFA should be applied in a way that meaningfully reduces risk without creating unnecessary friction.
| When Uniform MFA Creates More Friction Than Protection
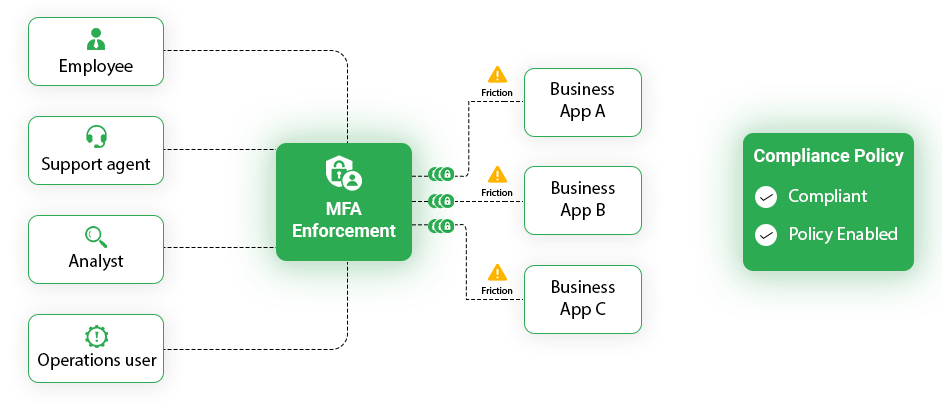
In many organizations, MFA adoption begins as a compliance-driven initiative. An audit requirement appears, a policy is written, and MFA is enabled broadly to demonstrate coverage. The simplest path is often to enforce MFA for everyone, on every login, regardless of context or access level.
In practice, this approach tends to create problems quickly.
Internal enterprise portals are accessed frequently throughout the day. Users log in to check dashboards, submit requests, review reports, or move between tools integrated through single sign-on. When MFA prompts appear on every login, users experience prompt fatigue. What was intended as a security control starts to feel like a constant interruption.
Support teams usually see the impact first. MFA reset requests increase. Exception requests appear for shared terminals, service accounts, or operational workflows. Over time, the organization begins to work around the control it just implemented. MFA remains technically enabled, but its effectiveness erodes as usability pressure mounts.
The core issue is not MFA itself. It is the assumption that all access carries the same level of risk.
| MFA as an Authentication Policy Decision
Effective MFA starts with policy design, not feature enablement. Before deciding when to prompt for an additional factor, it helps to step back and ask three basic questions:
- Who is the user?
- What level of access do they hold?
- How critical is the system or action being accessed?
These questions are practical, not theoretical. They map directly to how enterprise systems are structured.
A user who can view data but not modify it presents a very different risk profile than a user who can approve transactions, change configurations, or manage other identities. The authentication policy should reflect that difference.
When MFA is applied selectively, stronger authentication is introduced where potential impact is high, while lower-risk access paths remain streamlined. Security effort is concentrated where it reduces risk most effectively.
Keycloak supports this model by treating authentication as a configurable flow rather than a fixed sequence. MFA decisions can be made dynamically during login, without embedding conditional logic inside individual applications.
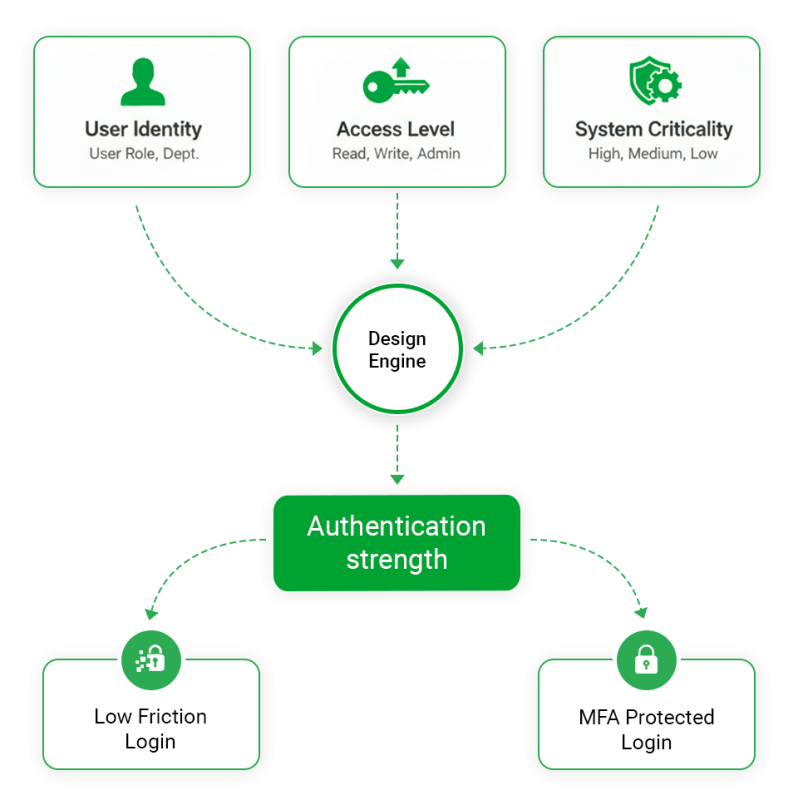
| Leveraging Keycloak Authentication Flows for Conditional Enforcement
Keycloak structures authentication as a sequence of execution steps within a flow. Each step can be required, conditional, or skipped based on runtime evaluation.
In a typical browser-based login flow, credentials are validated first. Once the user is authenticated, Keycloak evaluates available context such as both role and group membership. Based on that evaluation, the flow determines whether additional authentication is required.
If the user belongs to a role associated with elevated responsibility, the flow introduces an additional authentication step, commonly a time-based one-time password challenge. If no elevated condition is detected, authentication completes without further prompts.
For example, an operations engineer may belong to the ops-admin role. When they log in to a monitoring dashboard, Keycloak allows access with just a username and password. When the same user opens the Keycloak Admin Console or a production application, the authentication flow detects the ops-admin role and triggers a TOTP challenge before granting access. The identity is the same, but the authentication strength increases because the potential impact is higher.
From the user’s perspective, the login experience remains consistent. From a security perspective, authentication strength adapts to responsibility. This allows enterprises to centralize MFA policy enforcement within Keycloak while keeping applications free of authentication complexity.
| The Importance of Clear Access Models
Conditional MFA depends on accurate access modeling. Roles must clearly represent levels of responsibility and privilege.
In most enterprises, certain categories of users consistently represent higher-risk access. Identity administrators, operations teams with production access, finance users who can approve payments, and support users with elevated permissions should all be represented through clearly defined roles. Their actions can have outsized impact, whether through error or misuse.
At the same time, many users interact with systems in low-impact ways. They may view reports, submit requests, or monitor system status without the ability to change underlying data or configuration. Applying the same authentication friction to these users does little to reduce risk and often creates resistance to security controls.
Clear access models make MFA enforcement predictable, auditable, and aligned with business intent. Without them, conditional authentication becomes inconsistent and difficult to maintain.
Groups can still be used to organize users and assign roles, but MFA decisions should be driven by roles.
| A Practical Role-Based MFA Pattern
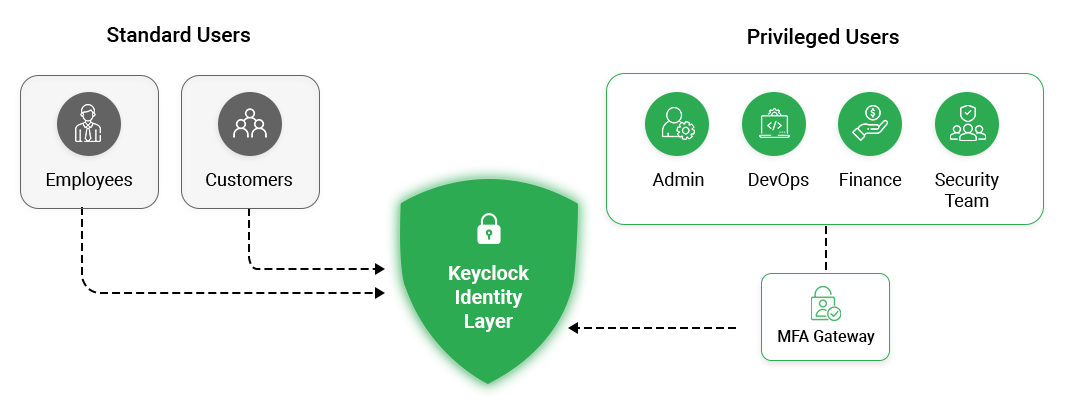
Many enterprise Keycloak deployments converge on a straightforward and maintainable pattern:
- All users authenticate using standard credentials
- Keycloak evaluates role membership during authentication
- Users with elevated or higher-risk roles are required to complete MFA
- Users without those roles proceed without additional prompts
This structure balances security and usability. Privileged access is protected by stronger authentication, while routine access remains efficient.
Keycloak’s built-in support for time-based one-time passwords enables this pattern without introducing external dependencies. MFA enrollment can occur during authentication, allowing users to configure their authenticator during initial access. As responsibilities change, role assignments can be updated without redesigning authentication flows.
| Strengthening Administrative Access Controls
Administrative access requires additional consideration. The Keycloak Admin Console controls users, roles, clients, integrations, and authentication policies themselves. Compromise at this level affects the entire identity platform, not just a single application.
For this reason, many enterprise security programs mandate MFA for all administrative access, regardless of other role-based conditions. Keycloak supports separate authentication flows for administrative access, allowing organizations to enforce stricter controls without affecting end-user login flows.
Separating administrative authentication ensures consistent protection for critical control planes while preserving flexibility elsewhere in the system.
| Introducing MFA Without Disrupting Operations
MFA rollout is as much an operational change as a technical one. Immediate global enforcement often exposes gaps in enrollment processes, recovery procedures, and user readiness.
A phased rollout typically proves more effective:
- Start with administrators and high-risk operational roles
- Stabilize MFA enrollment, recovery, and support processes
- Expand enforcement to additional roles as needed
Keycloak’s flexible flow model supports this evolution without requiring changes to application integrations or authentication endpoints.
| Avoiding Common Implementation Pitfalls
Enterprise MFA implementations often struggle when default authentication flows are modified directly, roles are poorly defined, or authentication logic is distributed across applications.
These issues increase maintenance overhead and make future changes risky. Centralizing authentication policy within Keycloak helps avoid these problems and simplifies long-term management. MFA becomes part of a coherent authentication strategy rather than an isolated control.
| Where WalkingTree Helps
WalkingTree supports enterprises in designing and implementing identity platforms that reflect real operational risk.
In Keycloak-based IAM engagements, this typically includes defining role models aligned with business responsibilities, designing authentication flows for conditional MFA enforcement, implementing dedicated authentication flows for administrative access, and integrating Keycloak with enterprise directories and applications.
WalkingTree also supports phased MFA rollouts to minimize disruption while ensuring authentication controls remain effective, auditable, and maintainable as environments scale.
| Conclusion
Multi-Factor Authentication is most effective when it reflects real enterprise risk. Applying MFA uniformly across all users may appear decisive, but it often introduces friction without delivering proportional security benefits.
Keycloak provides the flexibility to implement role-aware, policy-driven MFA. Strong outcomes depend on clear access models and thoughtful authentication design. When MFA enforcement aligns with responsibility and impact, organizations can strengthen security without compromising productivity.
When designed well, MFA becomes a natural extension of an enterprise identity strategy rather than an obstacle to getting work done. Want to apply MFA where it actually reduces risk, without adding friction for every user? Reach out to Us.
| FAQs
Role-aware MFA means enforcing Multi-Factor Authentication based on user roles and access risk instead of applying it uniformly. In Keycloak, roles represent business privilege. When users with elevated access authenticate, the system dynamically requires stronger verification, protecting critical systems while reducing friction for routine users.
Uniform MFA treats all users as equally risky. In large enterprise environments, this causes prompt fatigue, increased support tickets, and workflow disruption. Over time, users work around controls, weakening overall security posture even though the organization remains technically compliant.
Keycloak uses configurable authentication flows that evaluate role membership during login. If the user holds a high-risk role, the flow triggers TOTP or other MFA methods. Lower-risk users continue without extra prompts. This enables centralized, policy-driven MFA without modifying applications.
Clear access models and defined roles ensure conditional MFA is consistent and auditable. Without them, enforcement becomes unpredictable. Strong role definitions align authentication policies with business risk, ensuring strong authentication is applied only where potential impact is highest.
A phased rollout of role-based MFA works best. Start with administrators and high-risk roles, stabilize enrollment and recovery, then expand gradually. Keycloak supports this approach through flexible flows that strengthen enterprise security without disrupting users.


I really enjoyed your article, keep it like that, google will love it and rank it high, i am now a follower!