Blogs
Identity Federation Made Easy: Integrating Keycloak for Seamless Authentication
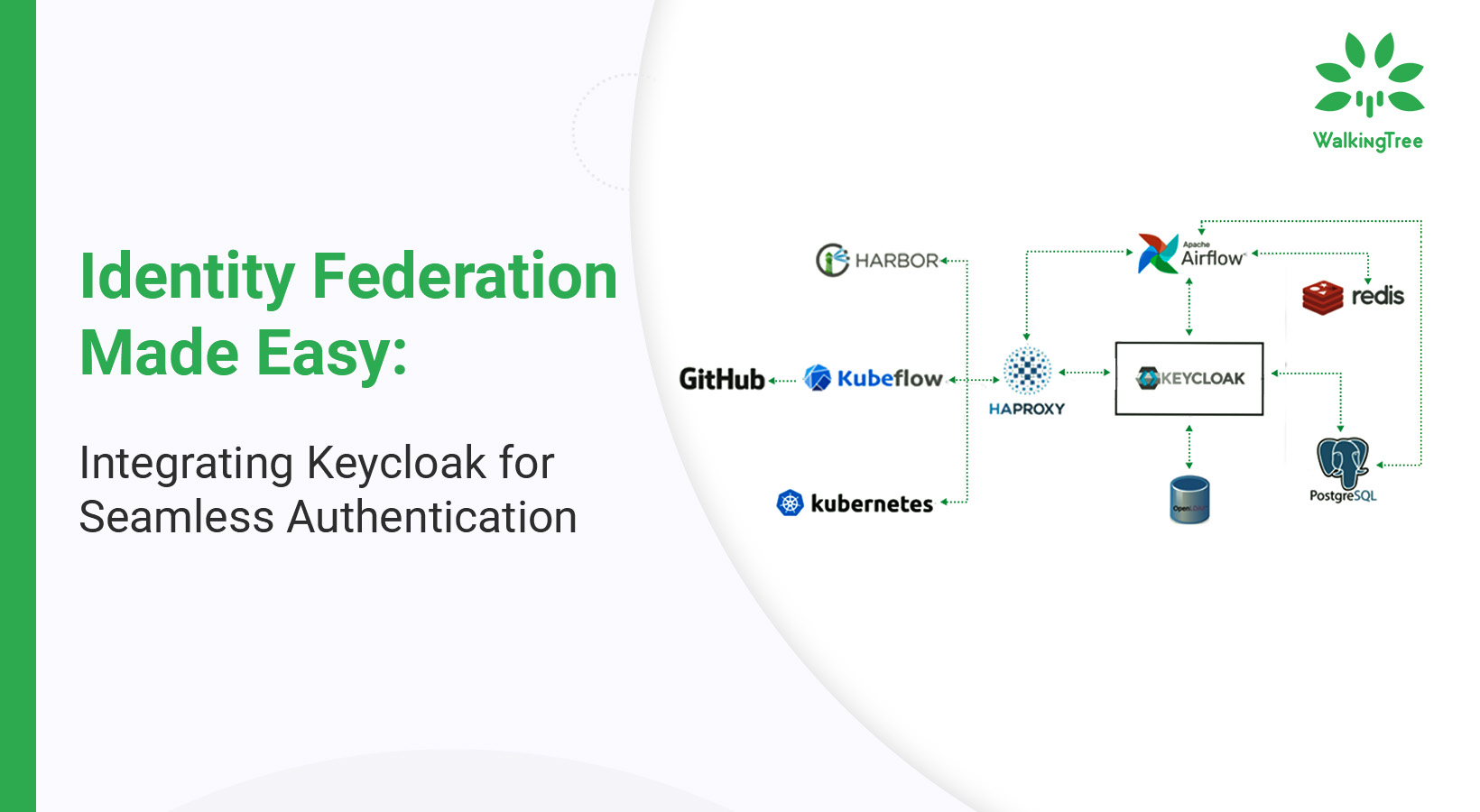
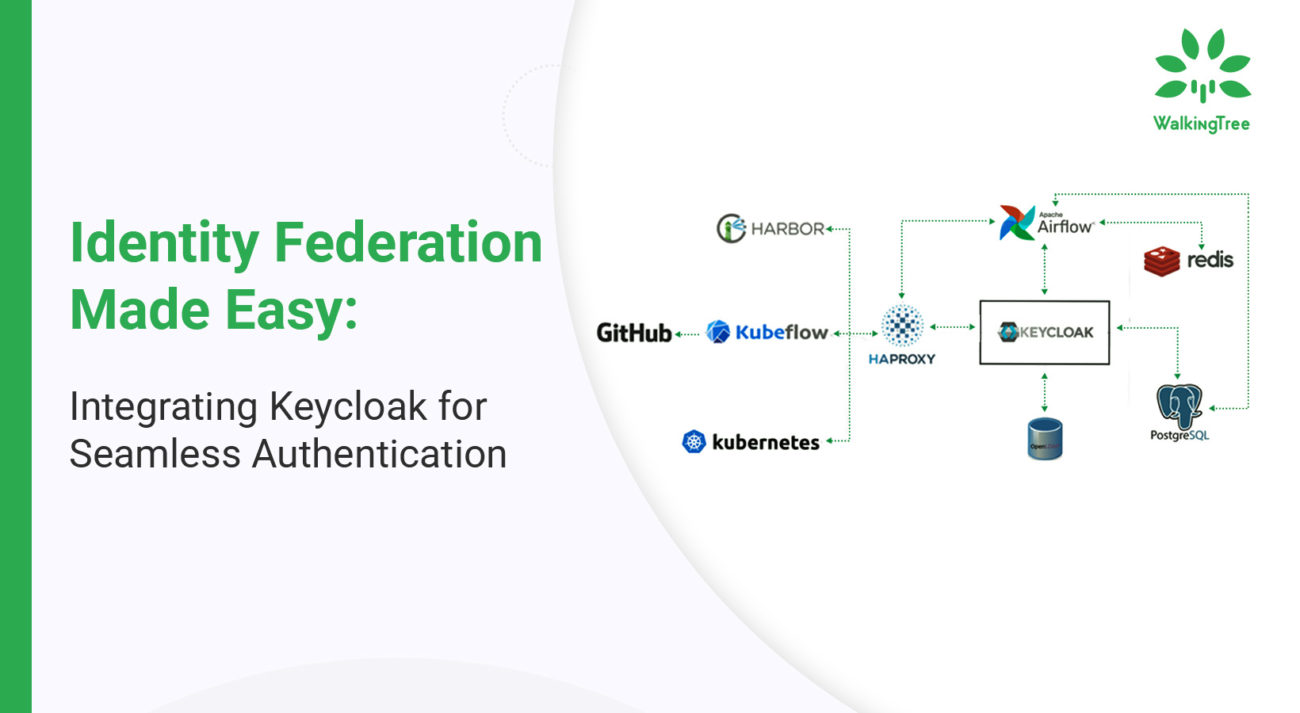
This comprehensive guide is designed to demystify the world of Identity Federation, with a special spotlight on Keycloak, a robust tool that simplifies identity management and authentication processes. This explores the fundamental principles of Identity Federation, provides a detailed procedure for configuring Keycloak as an Identity Provider, and outlines the optimal practices for the effective implementation of federated identity solutions.
Managing multiple usernames and passwords for various online services has become increasingly cumbersome for users. This is where identity federation emerges as a game-changer, allowing individuals to navigate through numerous applications and domains securely and conveniently with a single set of credentials. At the forefront of this revolution stands Keycloak, an innovative open-source identity and access management solution that streamlines authentication processes and enhances security.
Let’s explore how to configure Keycloak with external identity providers (IDPs) such as Google, Facebook, or LDAP, and adhere to best practices for implementing robust federated identity solutions.
Understanding Identity Federation
Identity federation is a sophisticated technology that enables users to access multiple applications or domains using a single authentication process. This not only simplifies the login experience for the user but also significantly enhances security by reducing the number of attack vectors associated with managing multiple passwords.
The Essence of Identity Federation
At its core, identity federation is based on trust. When two or more domains trust each other’s authentication procedures, they can share user credentials securely, allowing users to move seamlessly between services without the need for multiple logins. This is achieved through standards such as SAML (Security Assertion Markup Language), OAuth, and OpenID Connect, which facilitate secure exchanges of user authentication data between domains.
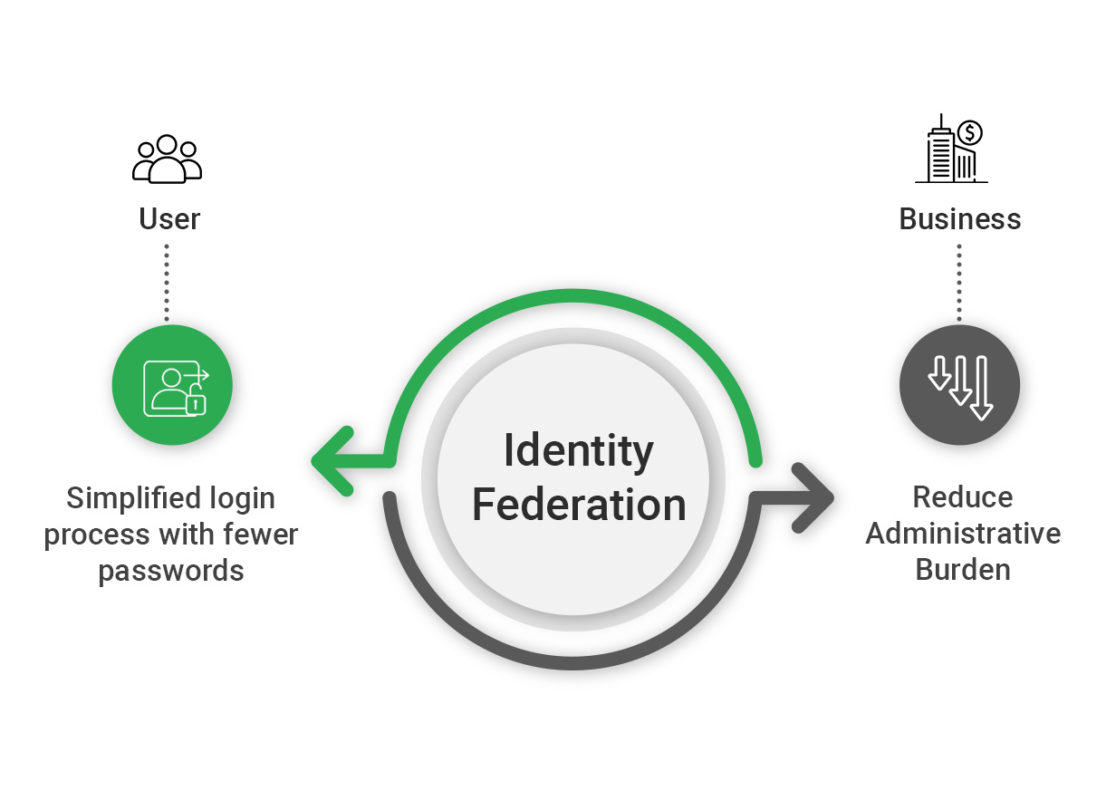
|The benefits of the Identity Federation
The benefits are clear for users, as a simplified login process with fewer passwords to remember leads to a smoother and more efficient online experience. Businesses, on the other hand, benefit from reduced administrative burdens associated with managing user accounts and credentials. Furthermore, identity federation can significantly bolster security by centralizing authentication systems, making it easier to enforce strong security policies and monitor suspicious activities.
By understanding the fundamental principles of identity federation, organizations can better appreciate the value that solutions like Keycloak bring to the table in creating a more secure, user-friendly digital environment.
The agility and speed of the Cloud Speed Layer come with their own set of challenges. The real-time processing requirement necessitates that data not only be processed swiftly but also securely, maintaining the integrity and confidentiality of information. Given the layer’s exposure to constantly changing data streams, it becomes a focal point for potential security vulnerabilities, highlighting the importance of robust vulnerability detection and patch management to ensure the system remains secure and reliable.
Keycloak Identity provider configuration
Configuring Keycloak as an identity provider (IdP) is a strategic move towards streamlining authentication mechanisms across various platforms. This section offers a detailed guide on integrating Keycloak with popular external identity providers, enhancing the authentication experience for users and administrators alike.
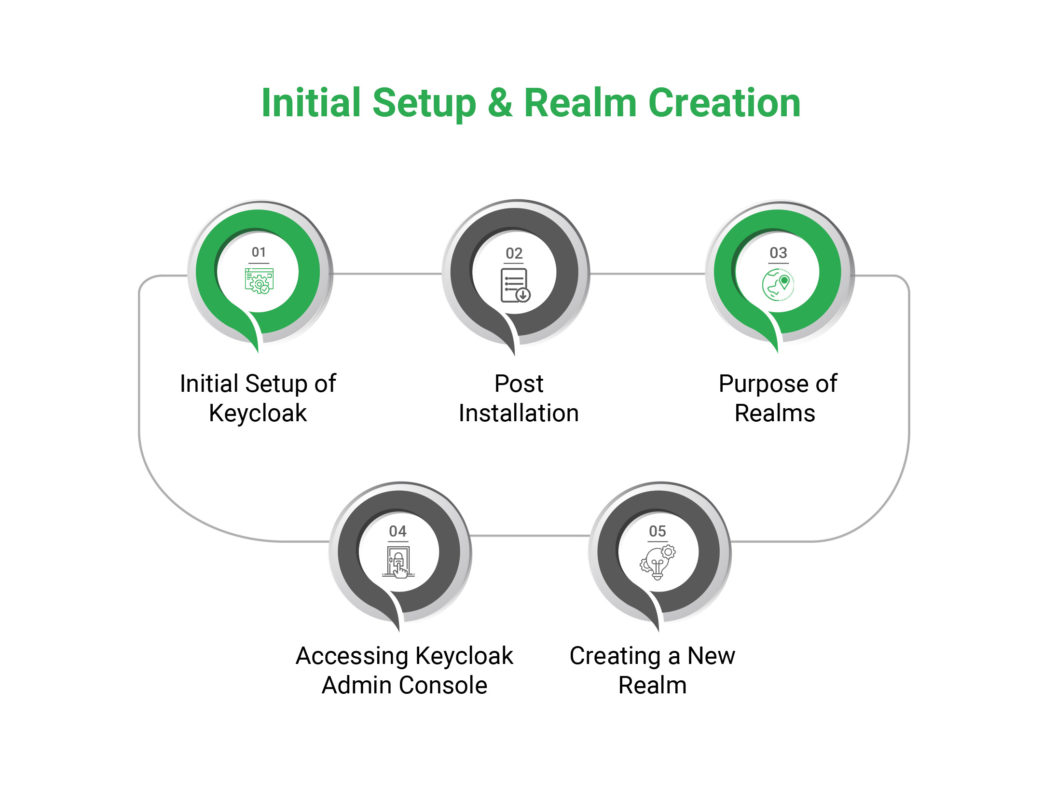
| Initial setup and realm creation
- Initial Setup of Keycloak: Download and install the Keycloak server to begin.
- Post-Installation: Proceed by creating a new realm.
- Purpose of Realms: Realms in Keycloak function as isolated environments where configurations are kept separate, facilitating multiple distinct authentication realms within the same Keycloak instance.
- Accessing Keycloak Admin Console: Log into the Keycloak administration interface.
- Creating a New Realm: Select ‘Add Realm’ and assign a unique name to encapsulate your federated identity configurations.
 |Integrating External Identity Providers
|Integrating External Identity Providers
Keycloak shines in its ability to seamlessly integrate with a plethora of external IDPs such as Google, Facebook, and LDAP directories, facilitating a broad spectrum of authentication options.
- Google and Facebook OAuth: For social IDps like Google and Facebook, the integration process involves:
- Registering your Keycloak instance as an application on the respective IDP’s developer console.
- Obtaining OAuth client ID and secret, and configuring these in Keycloak under the Identity Providers section.
- LDAP Directory: Integrating an LDAP directory is slightly more technical, requiring:
- Configuration of connection parameters such as URL, base DN (Distinguished Name), and administrator credentials.
- Mapping LDAP user attributes to Keycloak user attributes to ensure smooth data synchronization.
Through meticulous configuration, Keycloak can act as a powerful IdP, orchestrating seamless authentication across diverse external services.
|Federated Identity Best Practices
Implementing a federated identity system with Keycloak involves more than just technical configurations; it requires a strategic approach to ensure the authentication mechanisms’ security, efficiency, and usability. This section outlines the best practices for deploying Keycloak-based federated identity solutions.
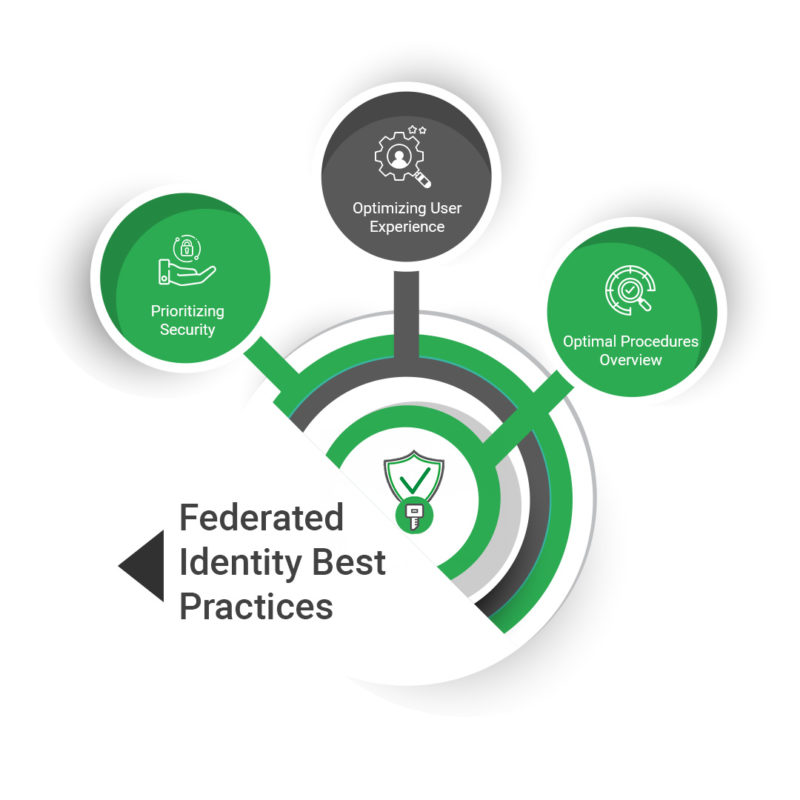
Prioritizing Security
In the realm of federated identity, security is paramount. The following practices are crucial in safeguarding the authentication process:
- Regular Security Audits: Conduct comprehensive security assessments to identify and rectify potential vulnerabilities within the authentication ecosystem.
- Secure Data Transmission: Utilize robust encryption methods, such as TLS, to protect data during transmission. Ensure all communications between Keycloak, the clients, and external IdPs are encrypted.
- Multi-Factor Authentication (MFA): Enhance security by implementing MFA. Keycloak supports various MFA mechanisms, including OTPs and hardware tokens, adding an extra layer of protection.
Optimizing User Experience
While security is critical, the success of a federated identity solution also hinges on its usability. A user-friendly system encourages adoption and satisfaction:
- Minimize Login Interruptions: Strategically implement SSO and session management to reduce unnecessary login prompts, ensuring a smooth user journey across services.
- Clear User Consent Interfaces: When sharing user information across domains, employ transparent and easily understandable consent mechanisms. Users should have clear control over what information is shared and with whom.
- Efficient Access Recovery: Design straightforward processes for password recovery and account management, minimizing user frustration and support tickets.
Optimal Procedures Overview
- Comprehensive Configuration Review: Regularly revisit and optimize Keycloak configurations to align with evolving security standards and organizational needs.
- User Education: Empower users with knowledge about security best practices and the benefits of federated identity systems. Informed users are less likely to engage in risky behaviors.
- Adaptability: Stay updated with the latest trends in identity management and be ready to adapt your Keycloak setup to incorporate new features and security measures.
By adhering to these best practices, organizations can create a federated identity environment that not only secures sensitive information but also offers an intuitive and efficient user experience.
Integrating Keycloak for identity federation represents a significant leap towards more secure, efficient, and user-friendly authentication systems. From configuring Keycloak with external identity providers, and adhering to federated identity best practices, organizations can harness the full potential of Keycloak to enhance their authentication.
The progression towards integrated authentication via Keycloak constitutes a tactical and beneficial endeavor, providing equilibrium between stringent security protocols and improved user interaction. With digital identity advancements, Keycloak emerges as a critical instrument in developing authentication mechanisms, facilitating the transition towards a more unified and secure digital ecosystem.