Customizable & Expandable
Identity Access Management solutions have a large number of extension points that you can use to deploy custom code. This feature lets you modify behaviours and even add new capabilities.
Keycloak - How it Works
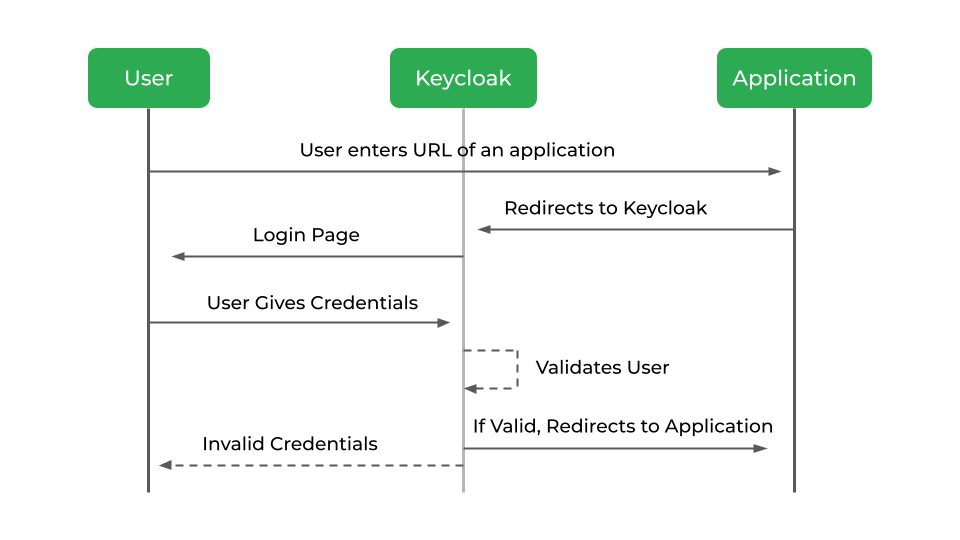
When the user tries to navigate to a protected application, he is first redirected to the Keycloak authentication page. Once he enters his login credentials, Keycloak will redirect the user to the application with a code.
The application exchanges this authorization code with an ID and access token. The application can then use this ID or access token to authenticate the identity of the user.
Looking for IAM solutions?
Keycloak - How it Works
Our Services - Identity management through Keycloak
Identity and Access Management
Manage user Identity and Access by creating custom roles and groups for user database – using this information to authenticate users.
Identity Brokering
Through Keycloak’s admin panel you can use Keycloak as a proxy between your users and another identity management provider.
External Identity Source Sync
Synchronize Keycloak with an external database. Using Keycloak User Storage API, create custom extensions for any user database.
Customize Pages
Customize all pages displayed by Keycloak using HTML markups and CSS styles. Use custom JS scripts as part of customization for limitless possibilities.
Keycloak Integration
Due to its support capabilities, we can integrate Keycloak on standard protocols like OAuth 2.0, OpenID Connect, and SAML 2.0.
Single Sign On
One time authentication. Users need to authenticated their identity only once and get access to multiple applications.

